Monday, 11 December 2023
Cybermobs for online academic bullying - a new censorship option to protect The Science™ ’s status-quo
Feedback to the presentation was positive, with the audience agreeing that it is necessary to formalise a critical space within universities where viewpoint diversity and boundary-breaking research can be promoted. For example, universities could consider how to support apolitical funding for adversarial research collaborations. Universities must also motivate for funding from government to address the lack of funding outside medicine for innovative, and potentially controversial, research. Without action to support such academic freedom, funders' biases will continue to constrain all research conflicting with their interests.
- The recently launched University of Austin
- FIRE Foundation for Individual Rights and Free Expression
- The Brownstone Institute
- Quilette
- Heterodox Academy
- Free Speech Union
- Academic Freedom for All
- Do Better Academia
- FreeX and LoofWired
- Academic Parity movement
- Speak Out Revolution
- Whistleblower Anti Bullying Network
I enjoyed learning from the audience, and hope to present to the Open Society in the not-too-distant future with in-depth research examples for academic cybermobbing. These may present interesting contrasts to the Emeritus Professor's case written about in 'Distinguishing online academic bullying'!
Tuesday, 26 September 2023
Noteworthy disparities with four CAQDAS tools: explorations in organising live Twitter (now known as X) data
QDAS tools that support live data extraction are a relatively recent innovation. At the time of our fieldwork, four prominent QDAS provided this: only ATLAS.ti™, NVivo™, MAXQDA™ and QDA Miner™ had Twitter data import functionalities. Little has been written concerning the research implications of differences between their functionalities, and how such disparities might contribute to contrasting analytical opportunities. Consequently, early-stage researchers may experience difficulties in choosing an apt QDAS to extract live data for Twitter academic research.
To ensure that each week's Twitter data extractions could produce much data for potential evaluation, we focused on extracting and organising communiqués from the national electrical company, the Electricity Supply Commission (Eskom). ‘Load-shedding’ is the Pan South African Language Board’s word of the year for 2022 (PanSALB, 2022), due to it most frequent use in credible print, broadcast and online media. Invented as a euphemism by Eskom’s public-relations team, load-shedding describes electricity blackouts. Since 2007, planned rolling blackouts have been used in a rotating schedule for periods ‘where short supply threatens the integrity of the grid’ (McGregor & Nuttall, 2013). In the weeks up to, and during, the researchers’ fieldwork, Eskom, and the different stages of loadshedding strongly trended on Twitter. These tweets reflected the depth of public disapproval, discontent, anger, frustration, and general concern.
QDAS packages commonly serve as tools that researchers can use for four broad activities in the qualitative analysis process (Gilbert, Jackson, & di Gregorio, 2014). These are (a) organising- coding sets, families and hyperlinking; (b) exploring - models, maps, networks, coding and text searches; (c) reflecting - through memoing, annotating and mapping; and (d) integrating qualitative data through memoing with hyperlinks and merging projects (Davidson & di Gregorio, 2011; Di Gregorio, 2010; Lewins & Silver, 2014).
Please comment below if you have any questions or comments regarding our paper?
Monday, 21 August 2023
Four categories for Anti-Bullying Apps (ABAs), with examples for each
There are many Anti Bullying Apps (ABAs) seeking to inform and assist recipients of cyber harassment. Some ABAs may even assist cyberbullies with curbing their anti-social behaviours. ABAs vary in their specific functions and features. These can be categorised into three groups [1]: (1) general protection, (2) information, and (3) reporting to authorities. This post suggests a fourth, (4) in-platform interventions (such as Instagram's anti-bullying tools). This accommodates tools that are distinct in being specifically developed to exist inside a particular platforms (such as WhatsApp, versus being a standalone app outside it). Such sub-apps (or tools) may also combine different aspects of the top three categories:
1 General protection
1.2 BullStop at https://www.bullstop.io/ aims to help young people's proactive combating of cyberbullying, and monitors social media accounts by regularly reviewing messages as they are received. It uses artificial intelligence for analysing these- flagging offensive content like abuse, bullying, insults, pornography, spam and threats. [1]
2 Information
2.1 ActionPoint aims to help families build stronger communication skills, set healthy boundaries for social media use, define a teen's cyberbullying risk and identify instances of cyberbullying. Ultimately its designers seek to decrease the negative outcomes associated with cyberbullying (view app's research at https://ysilva.cs.luc.edu/BullyBlocker/publications&posters.html).
2.2 Bully Mysteries (available as an Android package to download and install from https://apkcombo.com/bully-mysteries-4cv/udk.android.apptoapp.mystery.l1c5/) is an interactive mystery app that includes the chapter, 'The Case of the Cyberbully'- In it, 'A defenseless victim is being mercilessly harassed by someone. But who could it be and for what purpose? Katie and TC are extra motivated to solve this case and help protect those who can’t protect themselves!'. [6]
2.3 ClearCyberbullying (available as an Android package to download and install from https://apkcombo.com/clearcyberbullying/com.Clear.CyberBullying/) uses Drama Education for creating awareness on cyber-bullying among students and then develop an education video-games exploiting traditional “Puppet characters” or “shadow theatres” coming from the six partners countries. The project at https://www.clearcyberbullying.eu/ seems to have been discontinued. [6]
2.4 Cyberbullying by Grey Lab (available as an Android package to download and install from https://apkgk.com/com.iggnovation.cyberbull) provides information on 'what cyberbullying is, why it works and how to prevent it'. [6]
2.5 Cyberbullying First-Aid was developed in Germany by the klicksafe Youth panel for Android and Apple users. https://www.klicksafe.de/en/materialien/cyber-mobbing-erste-hilfe-app described how the app includes short videos from the coaches Tom and Emilia for recipients of cyberbullying. The app gives 'those affected concrete tips on how to behave, encourage them and accompany in the first steps to take action against cyberbullying. In addition to legal background information and links to anonymous counseling centers, there are tutorials on how to report, block or delete offensive comments on social media platforms such as Instagram, YouTube and TikTok or in the messenger WhatsApp.' The app is available in English, French, German, Luxembourgish, Lithuanian and Slovenian, dependant on the user's device's language setting. [6]
2.6 Cyberbullying Vaccine (available in Korea) aims to provide parents, guardians and other adults with an indirect experience of cyberbullying. [2]
2.7 Klikd at https://klikd.co.za/the-app/ covers many topics, ranging from how to manage tricky people online and cyberbullying, to online reputation to phone addiction. Each module contains multi-faceted components for keeping t/weens engaged throughout their learning journey. The app includes talks by teens, card games and quizzes, and offers plenty of opportunity for reflection. Parents and schools as also supported through updates. [9]
2.8 Know Bullying app at https://healthysafechildren.org/knowbullying-app gives US guardians and parents information on how to discuss online risks and cyberbullying with their children. The app was developed by the U.S. Department of Health and Human Services to; explain the warning signs of bullying, and to offer advice for parents on talking to their kids about bullying. It includes important strategies for preventing bullying for kids in varied age groups (3-6, 7-12, and older). [3]
2.9 Sit With Us is a US Apple app developed by a 16 year old. Natalie Hampton wanted to help pupils set up inclusive lunches with classmates who typically eat alone. [7]
2.10 SpeakOut! aims to help children and other vulnerable people with accessing the internet safely. The UK app presents storylines that tackle the topics of cyber bullying, grooming, sexting, fake news, body image and racism. The app was developed in response to 'the growing need for support specifically targeting 10-14 year olds as they face increased challenges as preteens and young teenagers growing up in a highly connected environment.' For example, the app tackles cyberbullying by featuring tools and techniques that help users recognise online bullying, and how to respond. [7]
2.11 Stand Up to Bullying shows an interactive educational video featuring Lucky Kat, The Kat Patrol, The Cheese Posse and Daren the Lion. It teaches children to identify the different types bullying and to know what to do when they see it happening. The app contains five (5) chapters of informative animation that cover verbal bullying, physical attack and nonverbal bullying. The final chapter instructs them on how to make a plan for when they see any of these situations. Each chapter closes with question and answer sections to support open discussion with kids and students. [7]
2+ Informational games
2.12 Cyberbully Zombies Attack at https://toucharcade.com/games/cyberbully-zombies-attack was developed by NetSmartz® Workshop, a program of the National Center for Missing & Exploited Children® and Gamelearn. The online game helps kids, tweens and teens learn how to handle cyberbullying [6]. It was funded by Sprint through its 4NetSafety(SM) program.
2.13 Cybersafe is a game for Android and Apple that Goffs School UK students created to help children deal with cyberbullying. [6] The app contains 3 fun mini games - each tackling a different issue chosen by the students: 'Detective Charlee: An endless flying game which teaches children to collect cyberbully evidence, by taking screenshots of nasty comments on social networks, to email to a trusted friend or adult. PaS$w0rdBlockr: A challenging puzzle game which encourages children to keep their passwords safe and be wary of people hacking their online accounts. Goof Run: An endless running game with helpful cyberbully advice along the way, set in a colourful chatroom.'
2.14 Professor Garfield Cyberbullying features a Garfield comic strip with examples of cyberbullying and advice on how to deal with it. These are followed by a short interactive quiz that tests what kids have learned. It is available on Apple. [6]
3 Reporting to authorities
3.2 BRIM: Bullying Reduction Intervention and Monitoring provides tools and resources to US teachers, principals, counselors, and others in school communities to help tackle bullying.
3.3 Bully Button from https://bullybutton.fortresgrand.com complements US schools' anti-bullying programs by providing a multi-platform process for administrative intervention in situations of; abuse, bullying, cyberbullying, and social aggression.
3+ Reporting to self
3.12 ReThink – Stop Cyberbullying at https://www.rethinkwords.com/whatisrethink is a non-intrusive service that seeks to detect and stop cyberbullying before it does damage. Its users are flagged to reconsider potentially offensive content before re-sharing it. [5]
4 Platform-specific
4.1 BullyBlock or BullyBlocker for Facebook (https://www.facebook.com/thebullyblocker) seems to have been superseded by the Action Point app (see 2.1) . BullyBlock resulted from research that 'designed, implemented and evaluated automated cyberbullying identification tools for social networks'. The mobile app for Facebook included several such tools. [1]
4.2 Instagram's Rethink and Restrict are described in https://www.bbc.com/news/technology-48916828. Rethink uses 'artificial intelligence to recognise when text resembles the kind of posts that are most often reported as inappropriate by users'. Rethink prompts users to pause and consider what they are saying before sharing content flagged as potentially being inappropriate. Restrict is 'designed to help teens filter abusive comments without resorting to blocking others - a blunt move that could have repercussions in the real world'.
4.3 Shushmoji® for WhatsApp is an anti-chat harassment resource (for Apple or Android users) that provides end-of-conversation stickers and information on tactics individuals can use against chat harassment. See general FAQs at https://www.createwith.net/shushmoji-app-faqs.
4.4 Vodafone’s #BeStrong Emoji Keyboard is available on Android devices. This keyboard developed from the Be Strong Online anti-bullying initiative. A suite of #BeStrong support emojis aimed help young people convey compassion and support to friends who are being bullied online. The idea for a support emoji was first brought to Vodafone by anti-bullying ambassador Monica Lewinsky. The app's emojis were chosen by 'almost 5,000 young people around the world, who identified with them as symbols of compassion and solidarity'. [7]
Conclusion
The examples of apps above are largely from the developed world's Anglo- and Asian spheres, with the full usability of these apps often being restricted to their country of origin (notably, Korea, the UK and US). Kindly let me know of any other interesting resources and/or ABAs in the moderated comments section below? Or you contact me directly. I will update this post on an ongoing basis with suitable recommendations for new apps/resources, plus new ones my research uncovers.
P.S. There are several apps listed in the resources below that are not highly-ranked for Google searches, nor available via the Apple or Android app stores (or may be hidden from searches from South Africa). These are Back Off Bullies [6], Be Cybersafe Game [6], Cyberbullying by Maple Tree [6], Cyberbully Hotline [6], Delete Cyberbullying [6], I Am Witness and Put an End to Cyberbullying [6].
N.B. The many discontinued anti-bullying apps suggest the importance of ongoing investment of human and financial capital. Sustaining ABAs availability requires costly resources to address code updates, app promotion and ongoing refinement.
Resources
[2] 'The application of anti-bullying smartphone apps for preventing bullying in South Korea' by Insoo Oh in Tackling Cyberbullying and Related Problems - Innovative Usage of Games, Apps and Manga.
[3] 'Most useful bullying apps' at https://famisafe.wondershare.com/anti-bullying/usefull-anti-bullying-apps-or-ideas-for-parental-control.html.
[4] 5 Anti-Bullying Apps Every Family Should Have
[5] Anti-bullying apps are popular, but do they work?, Wyman, Christina (2022) in Wired magazine features an interesting critique of ABAs' limits, and their potential value, https://www.wired.com/story/anti-bullying-apps-schools-children.
[8] Searching #Antibullyingapp via Instagram - https://www.instagram.com/explore/tags/antibullyingapp/
Thursday, 29 June 2023
Twitter Support must do better for helping celebrity and public victims of a global diet phishing scam!
This post presents the underwhelming example of reporting diet phishing accounts to Twitter Support as a way to spotlight the difficulties of tackling fraud via social media platforms. Hopefully publicly shaming @TwitterSupport will encourage its leaders to help address the global diet phishing scam properly, whilst also providing decent reporting options for celebrities and their representatives:
South African celebrities hijacked in fake diet adverts
A major factor in the “success" of this global scam (it has been running since 2014!) is the poor response from Facebook, Instagram, Twitter and other social media companies to formal requests to close fake accounts and their advertisement campaigns. Their ineffective responses are legally shortsighted: social media companies that repeatedly permit diet phishing ads on their platforms are complicit in a fraud, and possibly in the delict of passing off. For example, in South Africa, the diet phishing scam has undoubtedly harmed the reputation of Prof Tim Noakes and The Noakes Foundation through its fraudulent, direct misrepresentation, of fake products. These have certainly confused the public and @TheNoakesF has lost goodwill from the many victims of the fraud’s misrepresentation!Since Prof Noakes’ identity was first hijacked in 2020, The Noakes Foundation (TNF) and partners (such as Dr Michael Mol and Hello Doctor) have tried many options to stop the scam. For example, TNF developed and publicised content against it via blogposts, such as Keto Extreme Scams Social Media Users Out of Thousands. TNF also produced these videos: Professor Tim Noakes vs. Diet Phishing: Exposing a Global Scam with Fake Celebrity Endorsements, Dr Michael Mol highlighting Diet Scams and Prof Noakes Speaks Out Against The Ongoing Diet Scam. Sadly, The Noakes Foundation’s repeated warnings to the public don’t seem to be making much difference in preventing new victims!
American, Australian, British and Swedish celebs hijacked, too!
In the United States, the diet phishing scam has also stolen the identities of major celebrities. Most are in popular TV franchises: Oprah Winfrey (@Oprah), Dr Mehmet Oz (@DrOz) Dr Phil (@DrPhil), Dolly Parton (@DollyParton), Kelly Clarkson (@kellyclarkson), the Kardashian Family (@kardashianshulu + @KimKardashian), Kelly Osbourne (@KellyOsbourne), Chrissy Teigen (@chrissyteigen), Martha Maccallum (@marthamaccallum), Blake Shelton (@blakeshelton) and #TomSelleck 🥸. It’s a Magnum opus of fraud!Amazing female celebs in the United Kingdom have also seen their identities stolen. Diet phishing scammers have hijacked the IDs of Holly Willis (@hollywills), Amanda Holden (@AmandaHolden), Anne Hegerty (@anne_hegerty) and Dawn French (@Dawn_French). Even the British (@RoyalFamily) has not been immune, with the targeting of Catherine, the Princess of Wales (@KensingtonRoyal) and the Former Queen Elisabeth II, RIP and God Bless. Sadly, Meghan Duchess of Sussex, has been targeted too...
Down Under, well-known Australian personalities, such as its national treasure Maggie Beer (@maggie_beer) and Farmer Wants A Wife host Sam Armytage (@sam_armytage) have had their identities misused for fake #weightloss endorsements. And also Mr Embarrassing Bodies Down Under himself, Dr Brad McKay (@DrBradMcKay).
In Sweden, Dr Andreas Eenfeldt (@DrEenfeldt from @DietDoctor), another leader in the low carbohydrate movement, has been targeted in promotions of fake #keto products. Sadly, the fake ads seem to generate far more attention and action than his or my father's health advice!
N.B. The examples above are not extensive in terms of all victims. We largely know of celebrities in the Anglosphere whose identities were stolen, then featured in English language reports and related search engine results.
Deceptive "Tim Noakes" Twitter accounts market Keto Gummies
Just as the celebrity names stolen for the fake ads change often, so do the product names. A few examples of these fake names are Capsaicin, FigurWeightLossCapsules, Garcinia, Ketovatru and KetoLifePlus. Be warned that new "products" are added every month! One particularly common term used in the scammers' product names is "Keto Gummies". A recent Twitter search for "Tim Noakes keto gummies" suggested many fake accounts in Figure 1 (just the top view!), plus diverse "product" names.
Figure 1. Twitter search results for Tim Noakes keto gummies (fake product accounts) (20 June, 2023)
Twitter Support does not think fake accounts are misleading and deceptive?!
These accounts have clearly been setup to fraudulently market "keto gummies" by suggesting an association with "Tim Noakes". So, the logical response for any representative of The Noakes Foundation would seem to be reporting each fake account for violating Twitter’s misleading and deceptive identities policy, right?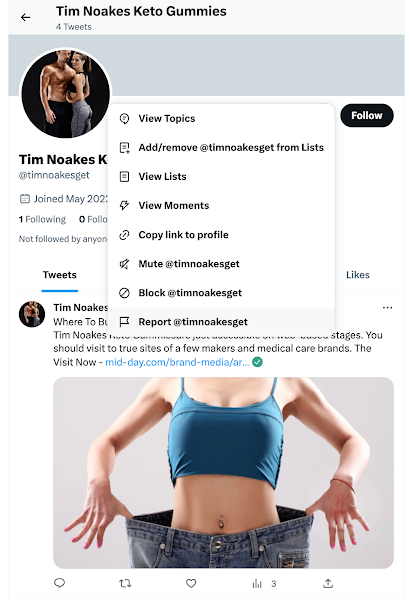
Fake Twitter accounts, including those below, were reported to Twitter, with support documentation:
@NoakesGumm28693 0327118996 @TimNoakesHoax 0327120384
@TimGummies 0327119602 @NoakesGumm91126 0327119675
@gummies_tim 0327120030 @TimNoakes_ZA 0327119741
@tim_gummies 0327118910 @NoakesSouth 0327118634
@timnoakesketo0 0327119362 @NoakesGumm22663 0327119487
In each case, @TwitterSupport replied that the following accounts are NOT in violation of Twitter’s misleading and deceptive identities policy. This would seem to contradict the obvious evidence that Tim Noakes' name has been hijacked by scammers for misleading victims with a fake product!
This "Tim Noakes keto gummies" Twitter account is not deceptive?!
Figure 3 shows a typical example of a fake account's style. It uses Tim Noakes' name, plus stock photography in marketing a non-existent product. It only tweeted on May the 24th, and is followed by one person. Any knowledgeable complaint reviewer would surely consider this to be a case of a scammer creating a misleading and deceptive account for gaming Twitter's search engine. However, Twitter Support does not agree, nor explain why in its generic correspondence around each scam account.
From stealing victims' banking details to delivering dubious products
Thursday, 22 June 2023
Recommendations for QDAS developers from 'Noteworthy disparities with four CAQDAS tools- explorations in organising live Twitter data', forthcoming
Outside the paper's scope, our software comparison also uncovered several suggestions that developers of these QDAS tools might follow to improve the user experience for Twitter researchers:
1 Make tweets easier to sort & link them to their original context
2 Provide more extensive support for modes and Twitter affordances
3 Support conversational analysis
4 Provide examples for live Twitter data analysis
5 Spotlight the black box of Twitter data organisation
6 Missing in extraction
Do let us know what you think of these suggestions by submitting a comment below, or contacting me.
Saturday, 15 April 2023
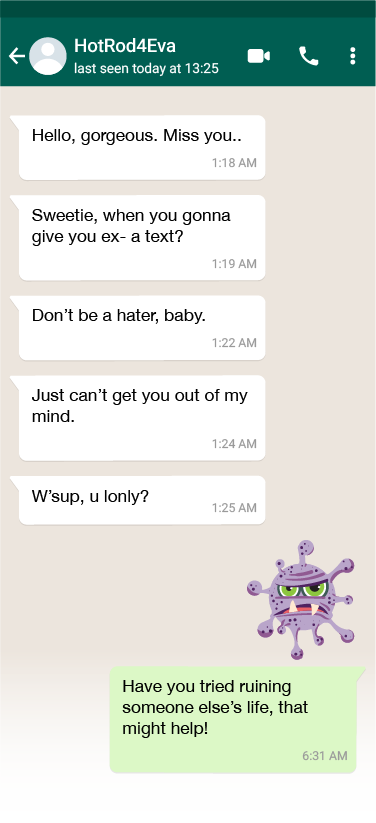
Use the Shushmoji app to learn anti chat harassment tactics and end anti-social conversations with WhatsApp chat stickers
| Stop silly troll! chat sticker example | Stop sinner! chat sticker example | |
|---|---|---|
 |  |
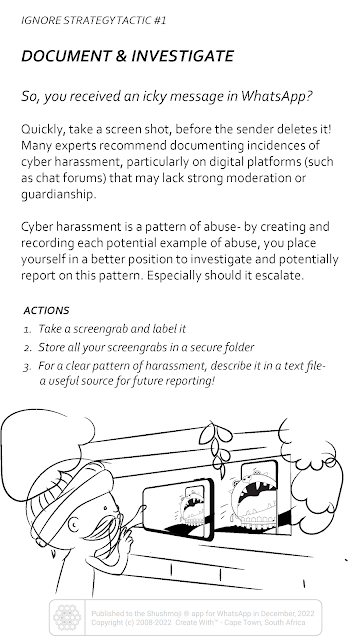
The Shushmoji app also offers twenty anti-chat harassment tactics cards. These fall under four strategies for stopping trolls: ignore, report, respond and prevent. Install the app to scroll through all twenty cards on your phone or tablet.
| Ignore strategy index card | Ignore tactic card |
|---|---|
Why develop a Shushmoji app?
Being silent echoes the conventional advice, Do Not Feed the Trolls (DNFTT). It reflects how there are many downsides to communicating with harassers, since they are likely to be mentally unstable (Barnes, 2018). Online trolls score low in the Big Five Personality scores of agreeability and conscientiousness, but score high in Dark Tetrad traits of- narcissism, Machiavellianism, sub-clinical psychopathy and/or everyday sadism. Attempting rational engagement with perpetrators of cyber harassment is likely to provoke retaliatory attacks in excess of the original abuse. This may be further escalated via circling cyber vultures and mobs. Such amplification is common to unmoderated platforms where destructive, hostile and bigoted behaviour is rewarded with likes and re-shares.
Create With Cape Town's end-of-conversation stickers were designed to support targets' ability to disengage from cyberbullies. Unlike the DNFTT tactic, it does not mute their voice and right-of-reply.
These chat stickers can help end chats-gone-bad, whilst showing trolls and their audiences what one thinks of their behaviour.
Support using the Shushmoji app
Shushmoji app credits
Shushmoji feedback
Alternately, hashtag #Shushmoji and #CreateWithCapeTown and give a shout-out to our Facebook, Instagram, LinkedIn or Twitter accounts. Cheers!








 orcid.org/0000-0001-9566-8983
orcid.org/0000-0001-9566-8983