Showing posts with label qualitative. Show all posts
Showing posts with label qualitative. Show all posts
Tuesday, 26 September 2023
Noteworthy disparities with four CAQDAS tools: explorations in organising live Twitter (now known as X) data
Written for researchers interested in extracting live X (formerly Twitter) data via Qualitative Data Analysis Software tools
QDAS tools that support live data extraction are a relatively recent innovation. At the time of our fieldwork, four prominent QDAS provided this: only ATLAS.ti™, NVivo™, MAXQDA™ and QDA Miner™ had Twitter data import functionalities. Little has been written concerning the research implications of differences between their functionalities, and how such disparities might contribute to contrasting analytical opportunities. Consequently, early-stage researchers may experience difficulties in choosing an apt QDAS to extract live data for Twitter academic research.
In response to both methodological gaps, we spent almost a year working on a software comparison to address the research question (RQ) 'How do QDAS packages differ in what they offer for live Twitter data research during the organisational stage of qualitative analysis?'. Comparing their possible disparities seems worthwhile since what QDAS cannot, or poorly, support may strongly impact researchers’ microblogging data, its organisation, and scholars’ potential findings. In the preliminary phase of research, we developed a features checklist for each package, based on their online manuals, product descriptions and forum feedback related to live Twitter imports. This checklist confirmed wide-ranging disparities between QDAS, which were not unexpected since they are priced very differently- ranging from $600 for an ATLAS.ti subscription, to $3,650 for a QDAMiner (as part of the Provalis Research’s ProSuite package, which also includes WordStat 10 & Simstat).
To ensure that each week's Twitter data extractions could produce much data for potential evaluation, we focused on extracting and organising communiqués from the national electrical company, the Electricity Supply Commission (Eskom). ‘Load-shedding’ is the Pan South African Language Board’s word of the year for 2022 (PanSALB, 2022), due to it most frequent use in credible print, broadcast and online media. Invented as a euphemism by Eskom’s public-relations team, load-shedding describes electricity blackouts. Since 2007, planned rolling blackouts have been used in a rotating schedule for periods ‘where short supply threatens the integrity of the grid’ (McGregor & Nuttall, 2013). In the weeks up to, and during, the researchers’ fieldwork, Eskom, and the different stages of loadshedding strongly trended on Twitter. These tweets reflected the depth of public disapproval, discontent, anger, frustration, and general concern.
QDAS packages commonly serve as tools that researchers can use for four broad activities in the qualitative analysis process (Gilbert, Jackson, & di Gregorio, 2014). These are (a) organising- coding sets, families and hyperlinking; (b) exploring - models, maps, networks, coding and text searches; (c) reflecting - through memoing, annotating and mapping; and (d) integrating qualitative data through memoing with hyperlinks and merging projects (Davidson & di Gregorio, 2011; Di Gregorio, 2010; Lewins & Silver, 2014).
To ensure that each week's Twitter data extractions could produce much data for potential evaluation, we focused on extracting and organising communiqués from the national electrical company, the Electricity Supply Commission (Eskom). ‘Load-shedding’ is the Pan South African Language Board’s word of the year for 2022 (PanSALB, 2022), due to it most frequent use in credible print, broadcast and online media. Invented as a euphemism by Eskom’s public-relations team, load-shedding describes electricity blackouts. Since 2007, planned rolling blackouts have been used in a rotating schedule for periods ‘where short supply threatens the integrity of the grid’ (McGregor & Nuttall, 2013). In the weeks up to, and during, the researchers’ fieldwork, Eskom, and the different stages of loadshedding strongly trended on Twitter. These tweets reflected the depth of public disapproval, discontent, anger, frustration, and general concern.
QDAS packages commonly serve as tools that researchers can use for four broad activities in the qualitative analysis process (Gilbert, Jackson, & di Gregorio, 2014). These are (a) organising- coding sets, families and hyperlinking; (b) exploring - models, maps, networks, coding and text searches; (c) reflecting - through memoing, annotating and mapping; and (d) integrating qualitative data through memoing with hyperlinks and merging projects (Davidson & di Gregorio, 2011; Di Gregorio, 2010; Lewins & Silver, 2014).
Notwithstanding the contrasts in the costs for different QDAS packages, it was still surprising how much the QDAS tools varied for the first activity, (a) ‘organising data’ in our qualitative research project: Notably, the quantum of data extracted for the same query differed, largely due to contrasts in the types and amount of data that the four QDAS could extract. Variations in how each supported visual organisation and thematic analysis also shaped researchers’ opportunities for becoming familiar with Twitter users and their tweet content.
Such disparities suggest that choosing a suitable QDAS for organising live Twitter data must dovetail with a researcher’s focus: ATLAS.ti accommodates scholars focused on wrangling unstructured data for personal meaning-making, while MAXQDA suits the mixed-methods researcher. QDA Miner’s easy-to-learn user interface suits a highly efficient implementation of methods, whilst NVivo supports relatively rapid analysis of tweet content.
We hope that these findings might help guide Twitter social science researchers and others in QDAS tool selection. Our research has suggested recommendations for these tools developers to follow for potentially improving the user experience for Twitter researchers. Future research might explore disparities in other qualitative research phases, or contrast data extraction routes for a variety of microblogging services. More broadly, an opportunity for a methodological contribution exists regarding research that can define a strong rationale for the software comparison method.
The authors greatly appreciate the SSRC's editor, Professor Stephen Lyon, advice on improving our final manuscript. We also thank The Noakes Foundation for its grant AFSDV02- our interdisciplinary software comparison would not have been possible without funding to cover subscriptions to the most extensive versions of MAXQDA Analytics Pro and QDA Miner. All authors are affiliated with the Cape Peninsula University of Technology (CPUT) and appreciate CPUT's provision of licensed versions of ATLAS.ti.
Please comment below if you have any questions or comments regarding our paper?
Please comment below if you have any questions or comments regarding our paper?
Labels:
academic
,
analysis
,
CAQDAS
,
QDAS
,
qualitative
,
research
,
social_network
,
software_comparison
,
Twitter
Location: Cape Town, Western Cape Province, RSA
Cape Town, South Africa
Thursday, 26 November 2015
Online Content Creation. Looking at students' social media practices through a #ConnectedLearning lens.
Written for researchers interested in students' social media practices, creative content production and how both can reflect indicators of the Connected Learning educational framework.
Cheryl Brown, Laura Czerniewicz and I wrote 'Online content creation. Looking at students' social media practices through a Connected Learning lens' for the Learning, Media and Technology journal. Our paper contributes to closing research gaps concerning: the Online Content Creation (OCC) practices of African university students; how indicators of the Connected Learning (CL) pedagogical framework are present in university students' non-formal creative productions; and the potential benefits that becoming digital creators might have for supporting students' social trajectories.
While previous studies have addressed creative production by university students for specific purposes, there is a research gap concerning OCC in the everyday lives of African university students. In analysing both the formal and informal ICT practices of 23 first year students at four South African universities, the use of online networks was pervasive. However, just three undergraduates described developing and/or using online presences to pursue interest-based activities.
We followed "Jake", "Vince" and "Odette" into their third year and learnt about: the social media they utilised; their trajectories; their linkages with career interests; and the types of online presences they created, maintained or discontinued. The pedagogical framework of CL proved an appropriate heuristic since all case studies spanned digital practices that, although non-formal, were: peer-supported (PS), interest-driven (ID) and academically oriented (AO). The cases also demonstrated the production-centred (PC) and shared-purpose (SP) of using openly networked (ON) new media for self-expression. PS, ID, AO, PC, SP and ON are all important indicators for CL.
There has been a tendency in CL literature to focus on secondary school youth, aged 12 to 18. We show how this emphasis can be extended to university, as students are likewise engaged in forming new interests and emergent social identities. By engaging in OCC, Jake, Vince and Odette could expand on the academic creative production interests they were formally taught. We describe how each student leveraged non-formal OCC practices for orientating towards new learning opportunities and social trajectories. Complementing these three student's formal production interests with rare OCC practices, seemed likely to give them an edge in our globally competitive society, as digital creators:
Jake used his productions as a student journalist, editor, poet and book writer to develop an online presence as a writer. He currently works as a communications trainee for a state agency. Vince's successful video production in an extra-curricular, online Ghetto Film School of LA course resulted in him being sponsored to present his short at the Sundance Film Festival Showcase. He currently works in multimedia and directs video-productions. Odette strategically developed separate online presences to promote her availability as an actor/model and scriptwriter. She also shares productions as a fiction writer, poet and personal journal diarist.
For more on African students' online content creation and social media use and how both reflected Connected Learning indicators, click on http://www.tandfonline.com/eprint/SqgVIjCFNzhQsXx5TKRF/full.
Cheryl Brown, Laura Czerniewicz and I wrote 'Online content creation. Looking at students' social media practices through a Connected Learning lens' for the Learning, Media and Technology journal. Our paper contributes to closing research gaps concerning: the Online Content Creation (OCC) practices of African university students; how indicators of the Connected Learning (CL) pedagogical framework are present in university students' non-formal creative productions; and the potential benefits that becoming digital creators might have for supporting students' social trajectories.
While previous studies have addressed creative production by university students for specific purposes, there is a research gap concerning OCC in the everyday lives of African university students. In analysing both the formal and informal ICT practices of 23 first year students at four South African universities, the use of online networks was pervasive. However, just three undergraduates described developing and/or using online presences to pursue interest-based activities.
We followed "Jake", "Vince" and "Odette" into their third year and learnt about: the social media they utilised; their trajectories; their linkages with career interests; and the types of online presences they created, maintained or discontinued. The pedagogical framework of CL proved an appropriate heuristic since all case studies spanned digital practices that, although non-formal, were: peer-supported (PS), interest-driven (ID) and academically oriented (AO). The cases also demonstrated the production-centred (PC) and shared-purpose (SP) of using openly networked (ON) new media for self-expression. PS, ID, AO, PC, SP and ON are all important indicators for CL.
There has been a tendency in CL literature to focus on secondary school youth, aged 12 to 18. We show how this emphasis can be extended to university, as students are likewise engaged in forming new interests and emergent social identities. By engaging in OCC, Jake, Vince and Odette could expand on the academic creative production interests they were formally taught. We describe how each student leveraged non-formal OCC practices for orientating towards new learning opportunities and social trajectories. Complementing these three student's formal production interests with rare OCC practices, seemed likely to give them an edge in our globally competitive society, as digital creators:
Jake used his productions as a student journalist, editor, poet and book writer to develop an online presence as a writer. He currently works as a communications trainee for a state agency. Vince's successful video production in an extra-curricular, online Ghetto Film School of LA course resulted in him being sponsored to present his short at the Sundance Film Festival Showcase. He currently works in multimedia and directs video-productions. Odette strategically developed separate online presences to promote her availability as an actor/model and scriptwriter. She also shares productions as a fiction writer, poet and personal journal diarist.
For more on African students' online content creation and social media use and how both reflected Connected Learning indicators, click on http://www.tandfonline.com/eprint/SqgVIjCFNzhQsXx5TKRF/full.
Labels:
creative production
,
media studies
,
OCC
,
qualitative
,
research
,
social_media
,
social_network
,
south_africa
,
students
,
university
,
web2.0
Location: Cape Town, Western Cape Province, RSA
Cape Town, South Africa
Friday, 5 October 2012
Improving the Student ICT Access and Use Project’s Coding Indices with Second Generation, Activity theory activity system components
Written for ICT researchers developing titles for coding indices.
Introduction
Using the components of an ‘activity system’ from the second-generation of Activity theory (Engeström, 2005) proved useful for creating more descriptive category titles in four coding indices that were developed during Laura Czerniewicz and Cheryl Brown’s research project Student ICT Access and Use (2004 -2012) project’s fourth phase (2011). This phase explored the first year university students’ formal and informal uses of Information Communication Technology (ICT). As the project gathered data from the ‘digital habitus’ of 26 students, it uncovered how they participated in many different activity systems. This long blog post explains how components of these activity systems were used to make more accurate and descriptive coding titles for each index.
Background
Phase four of the research project aimed to better understand how first year students from diverse social backgrounds were using ICT technologies, both formally and informally, at four South African universities in 2011. It sought to explore the ‘habitus’ (Bourdieau, 1986) of twenty six student subjects by analysing interviews, questionnaire feedback and day experience media (DEM) collected by a different researcher at each university for up to seven subjects.
To support efficient analysis across different media file types (video, audio and documents), these files were imported into qualitative research software. To code these media, four coding indices were developed after viewing students’ first and second interviews. The four indices could be used to code each subject’s: ‘past-’ (1), ‘present-’ (2) and ‘intended- ICT use’ (3), as well as common aspects of their feedback concerning ‘recent social media use’ (4). After publishing these indexes as Google documents, with supplementary posts on their development, I was asked to see whether Activity theory could serve a lens to improve the indexes’ category titles.
The Components of a Second Generation, Activity Theory ‘Activity System’
Activity theory (Engeström, 1987, 2001, 2005) has been used in many countries, including South Africa (Hardman, 2005, 2007), in order to understand the use of ICT in education (Kaptelinin and Nardi, 2006). Activity theory is a conceptual framework that is well suited to explain students’ use of online software in the complex social environment of university.
In Activity theory, the basic unit of analysis is an activity system, which in the first generation comprises a ‘subject’ who works with a ‘tool’ on a problem space, or ‘object’, to achieve an outcome that supports ‘objectives’ (Leontiev, 1974, 1981; Vygotsky, 1978, 1987; Wertsch, 1985). Second-generation Activity theory expands the activity system’s framework’s components to include ‘community’, ‘rules’ and ‘division of labour’ (Engeström, 1987).
An example of an activity system components in use is a student subject using a learning management system software tool as part of a common assignment (or problem space) to download an exercise. She does this with the the conscious objective of starting her assignment timeously. As a student, she is expected to observe rules; principles of control affording or constraining behaviour. If she does not submit her work on time, she will be penalised by losing marks. A division of labour that comprises a horizontal division amongst community members and a vertical division between the power- and status-holders also shapes the community’s actions. For example, the lecturer assigns an exercise to the class, which they must do individually. If he assigned a group project that would mark a change in the division of labour typically expected in class.
As this project’s indices reveal, its researchers explored many student activity systems; whether in the formal university environment or outside. The explanatory power of their components was then applied to all four indices, to see if they could better define category titles.
Updating coding index one, ‘Students' Past ICT Access and Use’.
The first index defined students’ exposure to ICT prior to university. This aligns with the Activity theory principle of development, which emphasises the importance understanding the origin and history of tool-appropriation by subjects. In this instance the index’s original titles did not reflect the learners’ secondary school context versus university: The index was divided into five categories, originally titled: ‘Demographics 0’, ‘Education 1.1’, ‘First ICT use 1.2’, ‘ Family history 1.3’ and ‘Access 1.4’. To clearly distinguish between these two contexts, the title ‘Education 1.1’ became ‘ICT education at secondary school 1.1’. By contrast, ‘Demographics 0’ became ‘Student's demographic details 0’ to highlight that the demographic details captured were for the students in 2011, not learners. It was also important to distinguish between the learners’ initial uses of ICT before university, so ‘First ICT uses 1.2’ became ‘Pre-varsity use of ICT tools 1.2’.
The tiles ‘Family 1.3’ and ‘Access 1.4’ were changed to be more descriptive, the former became ‘Use of tools in the family 1.3’, the latter ‘Site of access to ICT tools 1.4’.
For each index, the activity system components that each category featured were also highlighted under category headings. As an example, ‘Subject - Community - Rules - Division of Labour’ were added under the category ‘ICT education at secondary school 1.1’. This reflected the category’s focus on the learner subject whose formal exposure to ICT at school largely depended on the schooling community that they were part of, and its rules (or policies) influencing its learners’ access. By contrast, ‘Pre-varsity use of ICT tools 1.2’ focussed on each learner subject’s use of ICT tools, so only ‘Subject’ and ‘Tool’ were listed.
Changing coding index two, ‘Students’ Current ICT Use 2’
The second index was developed to code the students ownership of, as well as formal and informal access to, ICT tools and their academic or informal uses. Most students had access to a diverse range of tools which were provided through a community including their; University, parents or sponsors, peers or acquired through their own work. Although this was reflected through the sub-categories under the original ‘ICT ownership 2.1’ category title, this was not highlighted in the title itself, which was changed to ‘Student’s personal ICT ownership and/or access 2.1’ to better reflect different avenues of tool access. The other two category titles were changed to be more descriptive; from ‘ICT use 2.2’ and ‘Academic use 2.3’ to ‘Student’s personal ICT use 2.2’ and ‘Student's academic ICT access and use 2.3’, respectively.
A sub-category title was also changed to be more descriptive of community; ‘ICT help 2.34’ changed to ‘University, family and peer assistance with ICT 2.34’ thereby emphasising the varied members who provided assistance.
Revising coding index three, ‘Students’ Intended ICT Use 3’
The third index was used in coding transcriptions of students describing; the types of ICT tools and resources they desired, their future aims with ICT, how they plan to use social networks in the future and their current and future social work contributions. The original category titles were ‘ICT tools and resources wanted 3.1’, ‘Future ICT aims 3.2’, ‘Future social network use 3.3’ and ‘Subject's social work 3.4’. These were revised to highlight the role of the learner subject, becoming; ‘ICT tools and resources wanted by the student 3.1’, ‘The student's future ICT aims 3.2’, ‘The student's future social network desired use 3.3’ and ‘Student's social work 3.4’, respectively.
Modifying coding index four, ‘Students' Social Media Use 4’
The fourth index focussed on coding student feedback regarding their social media use for self-representation, friendship and achieving specific tasks (through its affordances), as well as rules they employed in using social media and their feelings about it. The original titles were; ‘Representations of self 4.1’, ‘Friendships and social media 4.2’, ‘Social media affordances 4.3’, ‘Personal social media rules 4.4’ and ‘Student feelings in relation to social media 4.5’. These were also modified to reflect the subject’s importance; ‘Student's representations of self 4.1’, ‘Student's friendships and social media 4.2’, ‘Student's perceptions of social media affordances 4.3’, ‘Student's personal social media rules 4.4’ and ‘Student's feelings in relation to social media 4.5’
In conclusion
Using the components of a second-generation Activity theory activity system proved useful as a lens to create more accurate and descriptive titles for the Student ICT Access and Use project’s coding indexes. Following a similar process may prove useful for ICT researchers creating or reviewing index titles.
References
Introduction
Using the components of an ‘activity system’ from the second-generation of Activity theory (Engeström, 2005) proved useful for creating more descriptive category titles in four coding indices that were developed during Laura Czerniewicz and Cheryl Brown’s research project Student ICT Access and Use (2004 -2012) project’s fourth phase (2011). This phase explored the first year university students’ formal and informal uses of Information Communication Technology (ICT). As the project gathered data from the ‘digital habitus’ of 26 students, it uncovered how they participated in many different activity systems. This long blog post explains how components of these activity systems were used to make more accurate and descriptive coding titles for each index.
Background
Phase four of the research project aimed to better understand how first year students from diverse social backgrounds were using ICT technologies, both formally and informally, at four South African universities in 2011. It sought to explore the ‘habitus’ (Bourdieau, 1986) of twenty six student subjects by analysing interviews, questionnaire feedback and day experience media (DEM) collected by a different researcher at each university for up to seven subjects.
To support efficient analysis across different media file types (video, audio and documents), these files were imported into qualitative research software. To code these media, four coding indices were developed after viewing students’ first and second interviews. The four indices could be used to code each subject’s: ‘past-’ (1), ‘present-’ (2) and ‘intended- ICT use’ (3), as well as common aspects of their feedback concerning ‘recent social media use’ (4). After publishing these indexes as Google documents, with supplementary posts on their development, I was asked to see whether Activity theory could serve a lens to improve the indexes’ category titles.
The Components of a Second Generation, Activity Theory ‘Activity System’
Activity theory (Engeström, 1987, 2001, 2005) has been used in many countries, including South Africa (Hardman, 2005, 2007), in order to understand the use of ICT in education (Kaptelinin and Nardi, 2006). Activity theory is a conceptual framework that is well suited to explain students’ use of online software in the complex social environment of university.
In Activity theory, the basic unit of analysis is an activity system, which in the first generation comprises a ‘subject’ who works with a ‘tool’ on a problem space, or ‘object’, to achieve an outcome that supports ‘objectives’ (Leontiev, 1974, 1981; Vygotsky, 1978, 1987; Wertsch, 1985). Second-generation Activity theory expands the activity system’s framework’s components to include ‘community’, ‘rules’ and ‘division of labour’ (Engeström, 1987).
An example of an activity system components in use is a student subject using a learning management system software tool as part of a common assignment (or problem space) to download an exercise. She does this with the the conscious objective of starting her assignment timeously. As a student, she is expected to observe rules; principles of control affording or constraining behaviour. If she does not submit her work on time, she will be penalised by losing marks. A division of labour that comprises a horizontal division amongst community members and a vertical division between the power- and status-holders also shapes the community’s actions. For example, the lecturer assigns an exercise to the class, which they must do individually. If he assigned a group project that would mark a change in the division of labour typically expected in class.
As this project’s indices reveal, its researchers explored many student activity systems; whether in the formal university environment or outside. The explanatory power of their components was then applied to all four indices, to see if they could better define category titles.
Updating coding index one, ‘Students' Past ICT Access and Use’.
The first index defined students’ exposure to ICT prior to university. This aligns with the Activity theory principle of development, which emphasises the importance understanding the origin and history of tool-appropriation by subjects. In this instance the index’s original titles did not reflect the learners’ secondary school context versus university: The index was divided into five categories, originally titled: ‘Demographics 0’, ‘Education 1.1’, ‘First ICT use 1.2’, ‘ Family history 1.3’ and ‘Access 1.4’. To clearly distinguish between these two contexts, the title ‘Education 1.1’ became ‘ICT education at secondary school 1.1’. By contrast, ‘Demographics 0’ became ‘Student's demographic details 0’ to highlight that the demographic details captured were for the students in 2011, not learners. It was also important to distinguish between the learners’ initial uses of ICT before university, so ‘First ICT uses 1.2’ became ‘Pre-varsity use of ICT tools 1.2’.
The tiles ‘Family 1.3’ and ‘Access 1.4’ were changed to be more descriptive, the former became ‘Use of tools in the family 1.3’, the latter ‘Site of access to ICT tools 1.4’.
For each index, the activity system components that each category featured were also highlighted under category headings. As an example, ‘Subject - Community - Rules - Division of Labour’ were added under the category ‘ICT education at secondary school 1.1’. This reflected the category’s focus on the learner subject whose formal exposure to ICT at school largely depended on the schooling community that they were part of, and its rules (or policies) influencing its learners’ access. By contrast, ‘Pre-varsity use of ICT tools 1.2’ focussed on each learner subject’s use of ICT tools, so only ‘Subject’ and ‘Tool’ were listed.
Changing coding index two, ‘Students’ Current ICT Use 2’
The second index was developed to code the students ownership of, as well as formal and informal access to, ICT tools and their academic or informal uses. Most students had access to a diverse range of tools which were provided through a community including their; University, parents or sponsors, peers or acquired through their own work. Although this was reflected through the sub-categories under the original ‘ICT ownership 2.1’ category title, this was not highlighted in the title itself, which was changed to ‘Student’s personal ICT ownership and/or access 2.1’ to better reflect different avenues of tool access. The other two category titles were changed to be more descriptive; from ‘ICT use 2.2’ and ‘Academic use 2.3’ to ‘Student’s personal ICT use 2.2’ and ‘Student's academic ICT access and use 2.3’, respectively.
A sub-category title was also changed to be more descriptive of community; ‘ICT help 2.34’ changed to ‘University, family and peer assistance with ICT 2.34’ thereby emphasising the varied members who provided assistance.
Revising coding index three, ‘Students’ Intended ICT Use 3’
The third index was used in coding transcriptions of students describing; the types of ICT tools and resources they desired, their future aims with ICT, how they plan to use social networks in the future and their current and future social work contributions. The original category titles were ‘ICT tools and resources wanted 3.1’, ‘Future ICT aims 3.2’, ‘Future social network use 3.3’ and ‘Subject's social work 3.4’. These were revised to highlight the role of the learner subject, becoming; ‘ICT tools and resources wanted by the student 3.1’, ‘The student's future ICT aims 3.2’, ‘The student's future social network desired use 3.3’ and ‘Student's social work 3.4’, respectively.
Modifying coding index four, ‘Students' Social Media Use 4’
The fourth index focussed on coding student feedback regarding their social media use for self-representation, friendship and achieving specific tasks (through its affordances), as well as rules they employed in using social media and their feelings about it. The original titles were; ‘Representations of self 4.1’, ‘Friendships and social media 4.2’, ‘Social media affordances 4.3’, ‘Personal social media rules 4.4’ and ‘Student feelings in relation to social media 4.5’. These were also modified to reflect the subject’s importance; ‘Student's representations of self 4.1’, ‘Student's friendships and social media 4.2’, ‘Student's perceptions of social media affordances 4.3’, ‘Student's personal social media rules 4.4’ and ‘Student's feelings in relation to social media 4.5’
In conclusion
Using the components of a second-generation Activity theory activity system proved useful as a lens to create more accurate and descriptive titles for the Student ICT Access and Use project’s coding indexes. Following a similar process may prove useful for ICT researchers creating or reviewing index titles.
References
Bourdieu, P. (1986). The forms of capital. In J. Richardson, Handbook of Theory and Research for the Sociology of Education (pp. 241-258). New York: Greenwood.
Engeström, Y. 1987, Learning by Expanding: An activity-theoretical approach to developmental research, Orienta-Konsultit Oy, Helsinki, Finland.
Engeström, Y. 2001, Expansive Learning at Work. Towards an Activity-Theoretical Reconceptualisation. University of London, London, England, UK.
Engeström, Y. 2005, Developmental work research: expanding activity theory in practice, Lehmanns Media, Berlin, Germany.
Hardman, J. 2007, "Making sense of the meaning maker: tracking the object of activity in a computer-based mathematics lesson using activity theory", International Journal of Education and Development using ICT, vol. 3, no. 4.
Hardman, J. 2005, "Activity Theory as a framework for understanding teachers' perceptions of computer usage at a primary school level in South Africa", South African Journal of Higher Education, vol. 25, no. 4, pp. 258-265.
Leontiev, A. 1981, Problems of the Development of Mind, Progress Publishers, Moscow.
Leontiev, A. 1974, "The Problem of Activity in Psychology", Soviet Psychology, vol. 13, pp. 4-33.
Kaptelinin, V. & Nardi, B. 2006, Acting with Technology: Activity Theory and Interaction Design, MIT Press, Cambridge, MA, USA.
Vygotsky, L. 1978, Mind in Society; The Development of Higher Psychological Processes, Harvard University Press, Cambridge, MA, USA.
Vygotsky, L. 1987, The collected works of L.S. Vygotsky. Plenum Press, New York, USA.
Wertsch, J. 1985, Culture, Communication and Cognition: Vygotskian Perspectives. Cambridge University Press, Cambridge, UK.
Labels:
academic
,
activitytheory
,
coding
,
education
,
qualitative
,
research
,
university
Location: Cape Town, Western Cape Province, RSA
Cape Town, South Africa
Monday, 11 June 2012
More changes I'd like to NVivo 9.
Written for NVivo 9's developers, QSR International, and their future NVivo users.
In 2011, I wrote Six key changes I'd like to see in NVivo 10. As NVivo 10's development nears completion, here's a further nine improvements for QSR International to consider implementing:
7. Provide a program execution status
It is useful for the user to know whether NVivo is initializing, running or shutting down. If the software seems to be unresponsive, seeing a status message, like: 'initializing', 'running', 'paused' or 'shutting down' would be helpful to the user and a better alternative than using Windows Task Manager to double-check.
8. Show closing down status messaging
Further, if NVivo is slow in closing, it would be useful to show how it is progressing. This is very important; if the user thinks that it has stalled, he or she may "force quit" the program when it prevents Windows shut down. As failing to close NVivo down properly can corrupt the project file, thereby costing the user much more time, the value of accurate status messaging (and even warning the user 'do not force quit') should not be underestimated.
9. Provide better communication when there are errors
Just as Microsoft impresses with problem messaging linked to solutions via its Solutions Centre, so too should NVivo consider linking its error messages to online help. For example when I was trying to fix an NVivo installation, the message "Database component did not initialise" could have been made far more helpful by linking straight to an FAQ page with possible solutions.
Given that NVivo users are qualitative researchers, it is unlikely that many of them have experience troubleshooting software. Providing us with more thorough and helpful error messaging will provide an improved user experience just where we experience most difficulty.
10. Report on third-party interference
I have noticed that NVivo's timebar may be paused (at 67%) for several minutes when an important Windows 7 process runs (such as deleting a backup snapshot, running a backup, et al.).
It would be helpful if the user could be shown that third-party software has interrupted NVivo, ideally in the software itself. Even a notification from Windows OS would be helpful.
11. Offer a back-up file option
Just as Apple's OS X Lion introduced Versions to protect users' files, so should NVivo consider adding a 'backup' option in addition to 'auto-save'. For users whose files became corrupted and had failed to create a back-up, this prompter could be very beneficial.
12. Provide a video rewind shortcut
For researchers working with many video interviews, a rewind F button shortcut would be great. I recently started work on a PC laptop and simply having the F7 (play/pause) shortcut available is a real timesaver {after moving from Mac, where I did not have this option}.
13. Allow the user to set a volume limit
The user should be given an option that sets a limit to NVivo's volume. In working with listening to mobile phone videos of varied audio-quality through headphones, this would be useful to protect my hearing as I move from soft, low-quality files to very loud, high-quality ones and forget to change volume.
14. Offer a pseudonym generator
As qualitative research invariably involves the ethical requirement to protect the privacy of one's subjects, it would be a nifty value-add if NVivo added a pseudonym generator.
In 2011, I wrote Six key changes I'd like to see in NVivo 10. As NVivo 10's development nears completion, here's a further nine improvements for QSR International to consider implementing:
7. Provide a program execution status
It is useful for the user to know whether NVivo is initializing, running or shutting down. If the software seems to be unresponsive, seeing a status message, like: 'initializing', 'running', 'paused' or 'shutting down' would be helpful to the user and a better alternative than using Windows Task Manager to double-check.
8. Show closing down status messaging
Further, if NVivo is slow in closing, it would be useful to show how it is progressing. This is very important; if the user thinks that it has stalled, he or she may "force quit" the program when it prevents Windows shut down. As failing to close NVivo down properly can corrupt the project file, thereby costing the user much more time, the value of accurate status messaging (and even warning the user 'do not force quit') should not be underestimated.
9. Provide better communication when there are errors
Just as Microsoft impresses with problem messaging linked to solutions via its Solutions Centre, so too should NVivo consider linking its error messages to online help. For example when I was trying to fix an NVivo installation, the message "Database component did not initialise" could have been made far more helpful by linking straight to an FAQ page with possible solutions.
 |
| Nvivo error message: 'Database component did not initialise' (10 April, 2012) |
10. Report on third-party interference
I have noticed that NVivo's timebar may be paused (at 67%) for several minutes when an important Windows 7 process runs (such as deleting a backup snapshot, running a backup, et al.).
 |
| NVivo stalled at 67 percent progress (6 June 2012) |
11. Offer a back-up file option
Just as Apple's OS X Lion introduced Versions to protect users' files, so should NVivo consider adding a 'backup' option in addition to 'auto-save'. For users whose files became corrupted and had failed to create a back-up, this prompter could be very beneficial.
12. Provide a video rewind shortcut
For researchers working with many video interviews, a rewind F button shortcut would be great. I recently started work on a PC laptop and simply having the F7 (play/pause) shortcut available is a real timesaver {after moving from Mac, where I did not have this option}.
13. Allow the user to set a volume limit
The user should be given an option that sets a limit to NVivo's volume. In working with listening to mobile phone videos of varied audio-quality through headphones, this would be useful to protect my hearing as I move from soft, low-quality files to very loud, high-quality ones and forget to change volume.
14. Offer a pseudonym generator
As qualitative research invariably involves the ethical requirement to protect the privacy of one's subjects, it would be a nifty value-add if NVivo added a pseudonym generator.
15. Provide an auto-save that does not auto-interrupt
I find auto-save very useful, and appreciate that this is probably an impossible request given the requirements of the 'save file' process, but it would be helpful if accepting the auto-save function did not automatically delete the incomplete timesheet entries a user was busy with. It would also be useful to be returned to the transcription block one was working on post auto-save, rather than being sent to the top by default. This can be irritating if working with a long interview and auto-save is set to be frequent.
I trust these ideas are constructive and helpful. Please let us know your thoughts in the comment box below, thanks.
I find auto-save very useful, and appreciate that this is probably an impossible request given the requirements of the 'save file' process, but it would be helpful if accepting the auto-save function did not automatically delete the incomplete timesheet entries a user was busy with. It would also be useful to be returned to the transcription block one was working on post auto-save, rather than being sent to the top by default. This can be irritating if working with a long interview and auto-save is set to be frequent.
Labels:
nvivo
,
qualitative
,
research
,
software
Location: Cape Town, Western Cape Province, RSA
Cape Town, South Africa
Thursday, 7 June 2012
Introducing the 'Coding index for Social Media Use 4'.
Written for researchers interested in the ICT Access and Use project's coding indices development.
After reviewing first year students' initial and second interviews in the fourth phase of the ICT Access and Use project, Laura Czerniewicz and I have prepared a fourth index to code conversations in which the following themes were discussed:
After reviewing first year students' initial and second interviews in the fourth phase of the ICT Access and Use project, Laura Czerniewicz and I have prepared a fourth index to code conversations in which the following themes were discussed:
- Representations of self;
- Friendships and social media;
- Social media affordances;
- Personal social media rules;
- Students’ feelings in relation to social media;
- Other roles of social media.
These discussions are outside the scope of the previous coding indices, which looked at students' past, current and future use of ICT.
In this posting, I describe the codes we decided on, their definitions, and then provide some examples of each code.
1. Representations of self.
Students spoke about how they chose to represent themselves online as themselves (their real names), using personas or with fake identities:
4.1 Identity representation
In this posting, I describe the codes we decided on, their definitions, and then provide some examples of each code.
1. Representations of self.
Students spoke about how they chose to represent themselves online as themselves (their real names), using personas or with fake identities:
4.1 Identity representation
This is about stating who they are online, who they represented themselves to be, literally.
Not all students used a 'genuine identity' online, but some chose an online profile type that was a 'persona' or even 'fake identity' online. Three examples were:
4.12 Type of username
The naming convention students used in selecting usernames would follow from their choice of identity. Most used some variation of their first and last names, while others chose a 'pseudonym': a pseudonym is different from a fake name as there is often a link between it and one's real name. Two examples of pseudonym use were:
4.13 Self disclosure
Another aspect of self-representation lay in the degree to which students were prepared to share the information they publish to social networks with all of its members or select groups of members. Student S was very selective about the people she chose to be her Facebook friends and said that she was comfortable with being very personal on it, because; 'For the people that are on Facebook, I feel as if I can share anything'. It is likely that she would not choose to limit the information that her Facebook friends could see by specifying a "limited profile view" for some groups of them.
By contrast, a researcher commented that she would not allow her parents to be Facebook friends with her. However, now that she could use Facebook's 'limited profile view' option for them, she might as she could then share select updates with her parents. Student R described the importance of knowing what your social network audience might see with the example of how a former high school prefect left his school and then his homosexuality was 'outed' by “Facebook Friends” who had used the photograph tagging functionality to identify him in gay bars.
Another aspect of self-disclosure is whether students allow their information on social networks to be searchable in these services' local search engines and/or external ones. The coding "Search settings for the Web 4.13.2" was added to cover instances where this was discussed.
2. Friendships and social media.
Not all students used a 'genuine identity' online, but some chose an online profile type that was a 'persona' or even 'fake identity' online. Three examples were:
- Student V used his “real” profile to publish writing on fanstory.com.
- Student O used another name (or persona) when she published her online diary to wattpad.com, as she did not want her intimate thoughts traced back to her by those who could recognise her handwriting.
- Student S and her best friend used a fake profile of a handsome guy to stalk prospective boyfriends' other potential girlfriends on facebook.com.
4.12 Type of username
The naming convention students used in selecting usernames would follow from their choice of identity. Most used some variation of their first and last names, while others chose a 'pseudonym': a pseudonym is different from a fake name as there is often a link between it and one's real name. Two examples of pseudonym use were:
- Student S' last name is an isiXhosa one, but she chose an English pseudonym at University that was easy for non-Xhosa speakers to use and remember.
- For his Facebook account, Student V uses a nickname of a film character he was given by his school friends and has not changed it as he believes that his friends would search for him using it.
4.13 Self disclosure
Another aspect of self-representation lay in the degree to which students were prepared to share the information they publish to social networks with all of its members or select groups of members. Student S was very selective about the people she chose to be her Facebook friends and said that she was comfortable with being very personal on it, because; 'For the people that are on Facebook, I feel as if I can share anything'. It is likely that she would not choose to limit the information that her Facebook friends could see by specifying a "limited profile view" for some groups of them.
By contrast, a researcher commented that she would not allow her parents to be Facebook friends with her. However, now that she could use Facebook's 'limited profile view' option for them, she might as she could then share select updates with her parents. Student R described the importance of knowing what your social network audience might see with the example of how a former high school prefect left his school and then his homosexuality was 'outed' by “Facebook Friends” who had used the photograph tagging functionality to identify him in gay bars.
Another aspect of self-disclosure is whether students allow their information on social networks to be searchable in these services' local search engines and/or external ones. The coding "Search settings for the Web 4.13.2" was added to cover instances where this was discussed.
2. Friendships and social media.
Students described the relationships between their face -to-face friendships and those existing online in these relatively open-ended codings:
4.21 Face-to-face versus online friendships
This code addresses the value students perceive online friendships to have, and how “real” they perceive them to be. Some students, like Student R, expressed a 'preference for face-to-face contact'. He would prefer someone to get to know him face-to-face than via his profile, 'The profile is an extension of oneself; it is still really important to be in touch with the real person. Facebook gives you many links and you can communicate with someone that is far away, but if you make Facebook your reality, then you sort of lose touch with actually sitting down and just having a glass of wine with someone and just chatting.'
A few students described the 'benefits of online friendships'. For example, Student K said that he believed his online friendships are real. There are people that he feels he can talk to and share with. There are other people that really encourage him. He felt that the relationships are realistic, rather than virtual. Student N said that she goes onto the internet to relieve her stress during her exams. When she relieves her stress, she does talk about the exams a lot with her friends on Facebook.
4.22 Friendship types by contact type
This coding covers the types of friends a student has on Facebook and on other types of social networks. For example, Student S said that only her closest friends and family are on BBM, while most of her friends are on Facebook and anyone can follow her on Twitter. So different levels of closeness are associated with different social networks.
4.23 Online social capital and self-esteem
This coding covers student feedback on the importance that online activities play in developing their social capital and self-esteem. Some students commented that when they joined Facebook, they felt under pressure to have 1,000 friends or more, to match their peers. Student K said that most people at are at the stage where he was on Facebook, when he first started. He noticed that many people had 1000 friends and he had a few, which he thought was a crisis. So, he went to Facebook pages that allow one to easily find new friends. He would go onto these pages and write 'Hi, just add me as a friend.' Then his Aunt told him, 'For real now, you need real friends, it's not cool to have many friends; who you don't know, who don't care and you won't even talk to.'
4.24 Types of exclusion
This coding deals with the extent to which students feel included or excluded from particular social networks due to them not having access to particular tools. A common example for South African students is those who do not have Blackberry phones and therefore feel left out of BBM conversations between their face-to-face friends.
3. Social media affordances.
A category for social media (software) affordances is useful to code student discussions about the distinct affordances that social media provides them. Since the most commonly discussed social networks were MXit, Facebook, Twitter and Google+, the categories reflect this by covering:
4.31 Facebook status updates
This code covers the types of updates students made as well as the reasons for the updates.
Many students spoke about their use of Facebook's status 'update' affordance and described the frequency with which they made updates. Student S said that on Facebook, you cannot have five status updates back-to-back as you need to give time for friends to comment. She normally updates her status on Facebook at least once every two days
Students also spoke about the reasons for updates. For example, Student K uses his updates for religious purposes; he comments on the challenges that people face and testifies on what God is doing for them.
The type of Facebook status update feedback they desired was also discussed; Student V, wanted his 'Facebook friends' to discuss the updates he made, as he is a lyricist and interested in what people think of the thoughtful updates he wrote.
4.33 Facebook: number of friends
This code deals with the number of friends affordance and the meaning this has for students.
As a 'social network' software, Facebook offers the affordance of allowing its users to view their friend's social networks or those which users have not set to be private. It also provides the total number of a user's "Facebook friends". Student Y wrote that she has 900 friends on Facebook, which came about, because she went on exchange. She met many groups on rotation. There are also family, friends and South Africans on exchange everywhere else. She emphasised that this was not by 'accept', 'accept', 'accept'!
4.34 Lists and circles
This code deals with the role that “friends’ lists” plays, either in Facebook (lists) or in Google + (Circles). Facebook offers an affordance for users to create "friend lists" and manage which lists get to view a user's updates. In speaking about how Student O's friendships online could be sustained, she stated that the fact that you are 'on their list, or that they are on hers, shows that you consider each other friends'. Even though you don't communicate with people often, you can still use the 'Family', group views. People will ask questions and one still feels that they are part of your life.
Google+, the social network that pioneered the concept of lists, shapes these as 'circles'. Student S spoke about this affordance, saying: In Facebook, Google+ believes that this is an add-on, while in their service one has to choose who one shares content with. You have "Circles"; a work circle, then school, then family. You separate (your contacts into) these groups and when you share something you can tick who you do, and don't, want to share with. People do not know what Circles you put them in.
4.35 Twitter affordances
This code looks specifically at how students understand Twitter affordances, and how they perceive these affordances to be different to other social media. While Facebook offers the affordance of 'friending' other users which they may approve or decline, Twitter offers "following", which is automatically accepted. Whilst "tweeting" is similar to updates, this does have its own syntax and benefits. Students discussed these affordances, for example. In discussing the merits of Twitter versus Facebook, Student R said that at least on Twitter, the people that he is following and the tweets that they put out are basically what he is looking at. So, at least he is following it, and it's not a lot of nonsense that one is not looking for (like on Facebook). By contrast, Student K stated that he finds Twitter "a bit dry" and prefers Facebook as you can see his profile and "meet me", while with Twitter, you just see who a person corresponds with, but do not get a good idea of what is going on.
4.36 MXit affordances
This code looks specifically at how students understand MXit affordances, and how they perceive these affordances to be different to other social media. Popular because of MXit's affordance of free messaging, this service was spoken about by Student R, who said that part of the reason that got him off MXit is that when you logon, there is probably a group of people he wants to chat to, but when you show that you are online, you get all these random messages. He related this to his concerns around asynchronous messaging: he has never really liked the realtime conversation where it is just all at once, and one has to do a relay; from someone to someone, come back... answer, answer, come back. It is too dispersed for him and he finds it difficult to follow these conversations.
4. Personal social media rules.
Some students spoke about developing rules that they used to govern when, where and how they would access social networks. For example, Student S said that she 'has her own rules for the different social networks'; there was a stage on Facebook when she would accept all friend requests and it reached a stage where she got to 1,500 friends. But they were all commenting on her wall, commenting on her personal pictures and asking her personal questions and she did not like this at all. So, she decided to clean up her Facebook and she would only have people that she knew personally; from primary school, high school or university. Not someone that she has never met before.
These codes are the indicators of the different social media rules:
4.41 Information flow control between services
In theory, students can publish a new tweet, blog post, picture, et al. and share this information after linking these services within their social media accounts (for example, this blog post is tweeted about via my Twitter account and that tweet is then published to my Facebook feed). This coding tracks student mentions of this practice.
4.42 Student media management
This coding is used where students speak about managing the types of media they select for publication to social media services. For example, Student S stated that when she updates Facebook it is for an audience. She always says, if you have a picture, keep it, why put it on Facebook? She only puts it up on Facebook if she wants other people to comment, so it's definitely for other people, to get their attention. Another example is Student R who spoke about regularly updating his profile; he had stages where he wants to update everything on his profile. When he sees a new movie that he likes, he will go under under information and add it. The latest thing he has done was with his CVs, he just went it to re-shuffle them around as he likes to place them in order of importance. He was having quite a bit of a Gossip Girl prediction. So he did not quite revamp it, you can see the influcence coming in as these characters pop-up. His profile will start to reflect what is going on in his life; before this his statuses were like about Vampire Diaries, his profile picture, his information reflected what he watches and stuff. This has become like a part of him and he updates it as he goes along; very regularly.
4.43 Social media terms of use
This code refers to student mention and understanding of social media terms of use; different terms of use apply to different social media services. For example, some will retain copyright of the material users submit, while others will share copyright or leave it as the users. When asked 'How does it work, in terms of copyright, do you know? Do you have any functions, settings or stuff? Or, do you basically go on the idea that somebody else is a writer and will respect your...)' Student V replied, 'The thing is that I have not checked it out. I have just been, like WOW!, 'writing site', bam, thrown it on there. And because there are so many people, I assume that the copyright means you get to keep your own work. Especially, because you can actually sell your work through this site.'
4.44 Privacy
This code deals with mentions of privacy and privacy settings on social media. Students described their perceptions of the privacy controls that social network software afforded them. Student S said when she first used Facebook, her profile was open and there were not as many privacy control settings. Now, if you go on, you will just see her name and what she is studying; no photos, most of her wall is 'off'.
Students discussed their concerns about privacy issues. Student S stated that she is big on 'Facebook stalking' other people. She knows that other people will stalk her and she does not want strangers to have access to her personal information.
It also includes students' descriptions of being searchable (or unsearchable) on a particular service or external ones. For example, if they talk about selecting settings on social media services that would make their profile searchable via that service and other search engines.
5. Student feelings in relation to social media
This cluster of codes refers to spoke about students feelings about or 'relationship' to one, or more, social media services. It was clear from the interviews that students form a relationship with different types of social media. There is at times a kind of personification happening.
4.51 Relationship to a social media service
For an example of a relationship to Facebook, Student S said that she definitely feels that because Facebook is so personal to her, that when they (Facebook) make a change to it, she feels like they are messing with her (personal) space!
4.52 Rationale and benefits of a social media service
Students did talk about their reasons for using specific social media services and their benefits. Student N said that Facebook was useful for support during University exams: She does feel that because all of her friends are in the same boat, that she gets support. One of her friends is writing and he also does Economics, so, you know, he was telling her the other day "you know, you better read...". So, it helps to know that there is someone going through what you are going through, not to just tell someone you are learning for exams and "Sorry, it will all work out". It helps a lot.
4.53 Understanding of services' use of personal data
Students could also describe their understanding of how social media services used their data:
For instance, Student K said that he was doing a course called 'Evidence-Based Management' in which they spoke about Facebook and Google. On Facebook, its Privacy Terms & Conditions state that you must update your account within 18 months or it will be terminated. So, they always want you update your infromation as they are making money off your profile and one's account details are provided to advertisers and they are making a lot of money from us using it.
4.54 Termination of service
A few students spoke about terminating their social media membership. Student S wrote that there was a time in the holidays that she was 'hating Facebook' and even deleted it for a couple of days. Facebook can be a way for people to ignore you; so she was not getting many wall-posts, she was updating her wall, saying things in status updates, but no-one was commenting. She felt a bit ignored, so she deleted Facebook. She got angry at it. Student K wrote that he wanted to 'stay away from Facebook for ever'; he finds Facebook draining as he was addicted to it. He would wake up with Facebook and go to sleep with Facebook. He wasted a lot of time on it; it has many applications and he received many invitations from dating sites which sent you profiles every day to your email. He needed space, so he stopped for three weeks and deleted his profile.
6. Other roles of social media
Code 5 covers the examples which emerged which demonstrated other roles played by social media in students’ lives.
One example is Student R, who spoke of the school that he went to, about 150 years old and tradition means a lot. One of the traditions was that prefects could lash their skivvies. Obviously now in modern times, this is counted as assault, so it was banned. However, it was happening behind closed doors. Someone had taken a video (of a beating), whatnot, and had threatened to go to Carte Blanche. The head boy was de-prefected, but then the rest of the prefects-body threatened to throw their badges away and there was this huge drama. This found its way onto Facebook and then the school said they would block Facebook and if you wanted to use it, you must go off campus. As a border, being at school during the week, there was not much Student R could then do with Facebook.
Hopefully, this introduction to the index is so thorough that you don't have any questions :) ! If not, please add yours as a comment below, thanks.
4.21 Face-to-face versus online friendships
This code addresses the value students perceive online friendships to have, and how “real” they perceive them to be. Some students, like Student R, expressed a 'preference for face-to-face contact'. He would prefer someone to get to know him face-to-face than via his profile, 'The profile is an extension of oneself; it is still really important to be in touch with the real person. Facebook gives you many links and you can communicate with someone that is far away, but if you make Facebook your reality, then you sort of lose touch with actually sitting down and just having a glass of wine with someone and just chatting.'
A few students described the 'benefits of online friendships'. For example, Student K said that he believed his online friendships are real. There are people that he feels he can talk to and share with. There are other people that really encourage him. He felt that the relationships are realistic, rather than virtual. Student N said that she goes onto the internet to relieve her stress during her exams. When she relieves her stress, she does talk about the exams a lot with her friends on Facebook.
4.22 Friendship types by contact type
This coding covers the types of friends a student has on Facebook and on other types of social networks. For example, Student S said that only her closest friends and family are on BBM, while most of her friends are on Facebook and anyone can follow her on Twitter. So different levels of closeness are associated with different social networks.
4.23 Online social capital and self-esteem
This coding covers student feedback on the importance that online activities play in developing their social capital and self-esteem. Some students commented that when they joined Facebook, they felt under pressure to have 1,000 friends or more, to match their peers. Student K said that most people at are at the stage where he was on Facebook, when he first started. He noticed that many people had 1000 friends and he had a few, which he thought was a crisis. So, he went to Facebook pages that allow one to easily find new friends. He would go onto these pages and write 'Hi, just add me as a friend.' Then his Aunt told him, 'For real now, you need real friends, it's not cool to have many friends; who you don't know, who don't care and you won't even talk to.'
4.24 Types of exclusion
This coding deals with the extent to which students feel included or excluded from particular social networks due to them not having access to particular tools. A common example for South African students is those who do not have Blackberry phones and therefore feel left out of BBM conversations between their face-to-face friends.
3. Social media affordances.
A category for social media (software) affordances is useful to code student discussions about the distinct affordances that social media provides them. Since the most commonly discussed social networks were MXit, Facebook, Twitter and Google+, the categories reflect this by covering:
4.31 Facebook status updates
This code covers the types of updates students made as well as the reasons for the updates.
Many students spoke about their use of Facebook's status 'update' affordance and described the frequency with which they made updates. Student S said that on Facebook, you cannot have five status updates back-to-back as you need to give time for friends to comment. She normally updates her status on Facebook at least once every two days
Students also spoke about the reasons for updates. For example, Student K uses his updates for religious purposes; he comments on the challenges that people face and testifies on what God is doing for them.
The type of Facebook status update feedback they desired was also discussed; Student V, wanted his 'Facebook friends' to discuss the updates he made, as he is a lyricist and interested in what people think of the thoughtful updates he wrote.
4.33 Facebook: number of friends
This code deals with the number of friends affordance and the meaning this has for students.
As a 'social network' software, Facebook offers the affordance of allowing its users to view their friend's social networks or those which users have not set to be private. It also provides the total number of a user's "Facebook friends". Student Y wrote that she has 900 friends on Facebook, which came about, because she went on exchange. She met many groups on rotation. There are also family, friends and South Africans on exchange everywhere else. She emphasised that this was not by 'accept', 'accept', 'accept'!
4.34 Lists and circles
This code deals with the role that “friends’ lists” plays, either in Facebook (lists) or in Google + (Circles). Facebook offers an affordance for users to create "friend lists" and manage which lists get to view a user's updates. In speaking about how Student O's friendships online could be sustained, she stated that the fact that you are 'on their list, or that they are on hers, shows that you consider each other friends'. Even though you don't communicate with people often, you can still use the 'Family', group views. People will ask questions and one still feels that they are part of your life.
Google+, the social network that pioneered the concept of lists, shapes these as 'circles'. Student S spoke about this affordance, saying: In Facebook, Google+ believes that this is an add-on, while in their service one has to choose who one shares content with. You have "Circles"; a work circle, then school, then family. You separate (your contacts into) these groups and when you share something you can tick who you do, and don't, want to share with. People do not know what Circles you put them in.
4.35 Twitter affordances
This code looks specifically at how students understand Twitter affordances, and how they perceive these affordances to be different to other social media. While Facebook offers the affordance of 'friending' other users which they may approve or decline, Twitter offers "following", which is automatically accepted. Whilst "tweeting" is similar to updates, this does have its own syntax and benefits. Students discussed these affordances, for example. In discussing the merits of Twitter versus Facebook, Student R said that at least on Twitter, the people that he is following and the tweets that they put out are basically what he is looking at. So, at least he is following it, and it's not a lot of nonsense that one is not looking for (like on Facebook). By contrast, Student K stated that he finds Twitter "a bit dry" and prefers Facebook as you can see his profile and "meet me", while with Twitter, you just see who a person corresponds with, but do not get a good idea of what is going on.
4.36 MXit affordances
This code looks specifically at how students understand MXit affordances, and how they perceive these affordances to be different to other social media. Popular because of MXit's affordance of free messaging, this service was spoken about by Student R, who said that part of the reason that got him off MXit is that when you logon, there is probably a group of people he wants to chat to, but when you show that you are online, you get all these random messages. He related this to his concerns around asynchronous messaging: he has never really liked the realtime conversation where it is just all at once, and one has to do a relay; from someone to someone, come back... answer, answer, come back. It is too dispersed for him and he finds it difficult to follow these conversations.
4. Personal social media rules.
Some students spoke about developing rules that they used to govern when, where and how they would access social networks. For example, Student S said that she 'has her own rules for the different social networks'; there was a stage on Facebook when she would accept all friend requests and it reached a stage where she got to 1,500 friends. But they were all commenting on her wall, commenting on her personal pictures and asking her personal questions and she did not like this at all. So, she decided to clean up her Facebook and she would only have people that she knew personally; from primary school, high school or university. Not someone that she has never met before.
These codes are the indicators of the different social media rules:
4.41 Information flow control between services
In theory, students can publish a new tweet, blog post, picture, et al. and share this information after linking these services within their social media accounts (for example, this blog post is tweeted about via my Twitter account and that tweet is then published to my Facebook feed). This coding tracks student mentions of this practice.
4.42 Student media management
This coding is used where students speak about managing the types of media they select for publication to social media services. For example, Student S stated that when she updates Facebook it is for an audience. She always says, if you have a picture, keep it, why put it on Facebook? She only puts it up on Facebook if she wants other people to comment, so it's definitely for other people, to get their attention. Another example is Student R who spoke about regularly updating his profile; he had stages where he wants to update everything on his profile. When he sees a new movie that he likes, he will go under under information and add it. The latest thing he has done was with his CVs, he just went it to re-shuffle them around as he likes to place them in order of importance. He was having quite a bit of a Gossip Girl prediction. So he did not quite revamp it, you can see the influcence coming in as these characters pop-up. His profile will start to reflect what is going on in his life; before this his statuses were like about Vampire Diaries, his profile picture, his information reflected what he watches and stuff. This has become like a part of him and he updates it as he goes along; very regularly.
4.43 Social media terms of use
This code refers to student mention and understanding of social media terms of use; different terms of use apply to different social media services. For example, some will retain copyright of the material users submit, while others will share copyright or leave it as the users. When asked 'How does it work, in terms of copyright, do you know? Do you have any functions, settings or stuff? Or, do you basically go on the idea that somebody else is a writer and will respect your...)' Student V replied, 'The thing is that I have not checked it out. I have just been, like WOW!, 'writing site', bam, thrown it on there. And because there are so many people, I assume that the copyright means you get to keep your own work. Especially, because you can actually sell your work through this site.'
4.44 Privacy
This code deals with mentions of privacy and privacy settings on social media. Students described their perceptions of the privacy controls that social network software afforded them. Student S said when she first used Facebook, her profile was open and there were not as many privacy control settings. Now, if you go on, you will just see her name and what she is studying; no photos, most of her wall is 'off'.
Students discussed their concerns about privacy issues. Student S stated that she is big on 'Facebook stalking' other people. She knows that other people will stalk her and she does not want strangers to have access to her personal information.
It also includes students' descriptions of being searchable (or unsearchable) on a particular service or external ones. For example, if they talk about selecting settings on social media services that would make their profile searchable via that service and other search engines.
5. Student feelings in relation to social media
This cluster of codes refers to spoke about students feelings about or 'relationship' to one, or more, social media services. It was clear from the interviews that students form a relationship with different types of social media. There is at times a kind of personification happening.
4.51 Relationship to a social media service
For an example of a relationship to Facebook, Student S said that she definitely feels that because Facebook is so personal to her, that when they (Facebook) make a change to it, she feels like they are messing with her (personal) space!
4.52 Rationale and benefits of a social media service
Students did talk about their reasons for using specific social media services and their benefits. Student N said that Facebook was useful for support during University exams: She does feel that because all of her friends are in the same boat, that she gets support. One of her friends is writing and he also does Economics, so, you know, he was telling her the other day "you know, you better read...". So, it helps to know that there is someone going through what you are going through, not to just tell someone you are learning for exams and "Sorry, it will all work out". It helps a lot.
4.53 Understanding of services' use of personal data
Students could also describe their understanding of how social media services used their data:
For instance, Student K said that he was doing a course called 'Evidence-Based Management' in which they spoke about Facebook and Google. On Facebook, its Privacy Terms & Conditions state that you must update your account within 18 months or it will be terminated. So, they always want you update your infromation as they are making money off your profile and one's account details are provided to advertisers and they are making a lot of money from us using it.
4.54 Termination of service
A few students spoke about terminating their social media membership. Student S wrote that there was a time in the holidays that she was 'hating Facebook' and even deleted it for a couple of days. Facebook can be a way for people to ignore you; so she was not getting many wall-posts, she was updating her wall, saying things in status updates, but no-one was commenting. She felt a bit ignored, so she deleted Facebook. She got angry at it. Student K wrote that he wanted to 'stay away from Facebook for ever'; he finds Facebook draining as he was addicted to it. He would wake up with Facebook and go to sleep with Facebook. He wasted a lot of time on it; it has many applications and he received many invitations from dating sites which sent you profiles every day to your email. He needed space, so he stopped for three weeks and deleted his profile.
6. Other roles of social media
Code 5 covers the examples which emerged which demonstrated other roles played by social media in students’ lives.
One example is Student R, who spoke of the school that he went to, about 150 years old and tradition means a lot. One of the traditions was that prefects could lash their skivvies. Obviously now in modern times, this is counted as assault, so it was banned. However, it was happening behind closed doors. Someone had taken a video (of a beating), whatnot, and had threatened to go to Carte Blanche. The head boy was de-prefected, but then the rest of the prefects-body threatened to throw their badges away and there was this huge drama. This found its way onto Facebook and then the school said they would block Facebook and if you wanted to use it, you must go off campus. As a border, being at school during the week, there was not much Student R could then do with Facebook.
Hopefully, this introduction to the index is so thorough that you don't have any questions :) ! If not, please add yours as a comment below, thanks.
Labels:
academic
,
affordances
,
choices
,
coding
,
output
,
qualitative
,
research
,
scholarly
,
south_africa
,
students
,
university
Location: Cape Town, Western Cape Province, RSA
Cape Town, South Africa
Monday, 30 April 2012
Avoid NVivo 9 installation interference from antivirus software.
Written for those struggling to install the embedded SQL software in an NVivo 9 installation.
The ICT Access and Use project recently purchased a PC laptop to work with a NVivo 9 project file I'd previously run on my Mac Pro desktop (running Parallels and Windows 7). I thought the installation of NVivo 9 would be simple on a laptop configured to operate within the University of Cape Town campus' network. However, there are three important actions that must be taken to avoid seeing this error message during your installation:
 |
| NVivo 9 installer "File is corrupt." error message. 29 April 2012. |
First, read the NVivo 9 software installation tips FAQ, which clearly states: "You should disable Antivirus, Antispam and Firewall applications (such as Norton Internet Security) before installing NVivo 9". I now know that an NVivo installation is not so simple and doing some preparation with background reading would have saved me much time and travel troubleshooting!
Second, un-install your Antivirus softwares: on our laptop, McAfee Anti-Virus was blocking changes to system files, which SQL was attempting to make as part of creating a virtual server to run SQL's databases locally. Once McAfee and NVivo were uninstalled, the fresh installation of NVivo installed Microsoft SQL Server 2008 R service pack 64 successfully.
Third, after successfully installation, reinstall your anti-virus software. In the case of a UCT laptop, the McAfee agent remained on the laptop after un-installation, and I contacted ICTS for instructions on how to reinstall the Antivirus software.
While you can successfully install NVivo without completing the SQL installation, you will not be able to run your project files locally. NVivo's open file function will ask you to connect to an NVivo server or will show the following error message when you try to launch NVivo from a local project file:
 |
| NVivo 9 standalone local connection error message. 29 April 2012. |
Special thanks to Ferdi (from Fimex - Softec) for identifying that anti-virus software was causing this problem and to Michael Harris (UCT ICTS Acquisitions Department) for fixing it.
Labels:
installation
,
nvivo
,
qualitative
,
research
,
software
Location: Cape Town, Western Cape Province, RSA
Cape Town, South Africa
Monday, 2 April 2012
New codings for the ICT Access and Use Research Project's fourth phase.
Written for researchers interested in the ICT Access and Use Project's coding indices' development.
Three months after making the initial coding indices for the fourth phase of the ICT Access and Use project publically available, I have just updated indices for "Past -", "Current -" and "Future ICT Use" to reflect the subsequent additions to our NVivo 9 project file's nodes (as illustrated below). These coding additions were necessary to reflect new insights from our research subjects' first and second interviews. They are described below under their relevant index:
Personal ICT Use coding index changes
Nodes were added for "Other ICT exposure 1.15" and "Self-taught 1.16" as not every student received formal schooling in ICT: for an example of 1.15; A Fort Hare university student had never had professional or formal classes in computing. For 1.16, the only training a Rhodes University student had was teaching himself; he fixed his family's computers himself. And a University of the Free State student "used to touch the home computer" to teach herself.
I thought it was a bit old school for freshers in 2011, but was suprised when MS Dos was mentioned as a first operating system! So, the node "MS Dos 1.26.4" was added.
One student accessed computers outside school and home at secondary school (hence "Internet cafe 1.43"), two students volunteered information on why they got mobile phones ("Why get a mobile phone 1.21.3"), another spoke about one's first computer tablet ("First tablet 1.28").
Current ICT Use coding index changes
The largest index saw the most revisions. Given the research project's interest in the use of mobile phones, the most important change was adding nodes that would allow the research team to track the most common platforms used to access online services and apps ("Platforms used in access 2.26" included "Computer 2.26.1", "Laptop 2.26.1.1", "Desktop 2.26.1.2", "Mobile 2.26.2" and "Tablet 2.26.3").
I also added the online services ("Webmail 2.21.13", "Music downloads 2.21.14", "Whatsapp 2.21.15", "Online forums 2.21.16", "YouTube 2.21.17", "Snap2 2.21.18", "Shazaam 2.21.19", "Online radio stream 2.21.20") and mobile phone apps ("Cognician 2.22.10" and "ToGo 2.22.11")recently mentioned by students. I also added the node "Does not use apps on mobile 2.22.9" to cover those students who explicitly stated that they did not download and/or use mobile apps.
Given the prevalence of iPods, I had to add "Music players 2.15.4" under the category "Other ICT owned"! Some students mentioned that they had "Access to ICT at home 2.17", while "Multitasking 2.23.9" was added as a theme that kept cropping up in students' use, for example of social media in the background as they worked on assignments.
The line between the use of social media for social and academic use is becoming blurred, as students report using social networking tools for both formal and informal academic work. This seems largely to be due to social media's affordances for ease of communication, efficient creation of academic groups and even saving money on MXit. This was reflected in student interviews and nodes for "Status update 2.24.10", "Messaging 2.24.11" and "Friending 2.24.12" were added, which could be applied to tracking affordances typical of social media.
Some first-year students also volunteered a fair amount of information on their preferences for response times ("Availability and feedback speed 2.25.11"), what they preferred to access services on ("Service preference 2.25.12"), how they felt about losing network access ("Mobile network access 2.25.13") and whether they experienced any limitations from their cellular provider ("Service limits 2.25.14").
Several students described having problems when using photocopying equipment for the first time ("Photocopies 2.31.7") and the importance of formal provision of either analogue and/or digital course material ("Textbooks and course reader 2.31.6").
Interviews revealed a wider range of actions with university software than initially identified, so the following nodes were added: "Group practicals 2.33.10", "Lecture notes 2.33.11", "Catch up missed classes 2.33.12", "Read announcements 2.33.13" and "Question and answer 2.33.14". And the following nodes were added under phases and types of academic use; "Frequency and duration of use 2.35.7", "Desired use 2.35.8" and "Self taught 2.35.9".
Future ICT Use coding index
Due to having recently upgraded mobile, laptop or other ICT technology and/or experiencing financial constraints, some students indicated that they did not want an upgrade ("No new mobile phone upgrade desired 3.11.2", "No new laptop upgrade desired 3.12.2" and "No other ICT desired 3.13.2").
Some students spoke about their ambitions at university ("University ambitions 3.24"), as well as the services they wanted to be on ("Academic services 3.31.1" and "Personal services 3.31.2"). Another University of Cape Town student mentioned his community involvement and promotion of ICT, so the node "Community involvement 3.4" was added to reflect this.
Lastly, a node "Play at Conferences 4" has been added to track the most interesting segments of student interviews. These are intended to be exported and formatted for playing at conferences by the project's research lead, Laura Czerniewicz, or principal investigator, Cheryl Brown.
Three months after making the initial coding indices for the fourth phase of the ICT Access and Use project publically available, I have just updated indices for "Past -", "Current -" and "Future ICT Use" to reflect the subsequent additions to our NVivo 9 project file's nodes (as illustrated below). These coding additions were necessary to reflect new insights from our research subjects' first and second interviews. They are described below under their relevant index:
Personal ICT Use coding index changes
 |
| Scribbled changes to the previous coding index for Past ICT Use 1 (30 March, 2012) |
Nodes were added for "Other ICT exposure 1.15" and "Self-taught 1.16" as not every student received formal schooling in ICT: for an example of 1.15; A Fort Hare university student had never had professional or formal classes in computing. For 1.16, the only training a Rhodes University student had was teaching himself; he fixed his family's computers himself. And a University of the Free State student "used to touch the home computer" to teach herself.
I thought it was a bit old school for freshers in 2011, but was suprised when MS Dos was mentioned as a first operating system! So, the node "MS Dos 1.26.4" was added.
One student accessed computers outside school and home at secondary school (hence "Internet cafe 1.43"), two students volunteered information on why they got mobile phones ("Why get a mobile phone 1.21.3"), another spoke about one's first computer tablet ("First tablet 1.28").
Current ICT Use coding index changes
 |
| Marked changes to the initial coding index for Current ICT Use 2 (30 March, 2012) |
The largest index saw the most revisions. Given the research project's interest in the use of mobile phones, the most important change was adding nodes that would allow the research team to track the most common platforms used to access online services and apps ("Platforms used in access 2.26" included "Computer 2.26.1", "Laptop 2.26.1.1", "Desktop 2.26.1.2", "Mobile 2.26.2" and "Tablet 2.26.3").
I also added the online services ("Webmail 2.21.13", "Music downloads 2.21.14", "Whatsapp 2.21.15", "Online forums 2.21.16", "YouTube 2.21.17", "Snap2 2.21.18", "Shazaam 2.21.19", "Online radio stream 2.21.20") and mobile phone apps ("Cognician 2.22.10" and "ToGo 2.22.11")recently mentioned by students. I also added the node "Does not use apps on mobile 2.22.9" to cover those students who explicitly stated that they did not download and/or use mobile apps.
Given the prevalence of iPods, I had to add "Music players 2.15.4" under the category "Other ICT owned"! Some students mentioned that they had "Access to ICT at home 2.17", while "Multitasking 2.23.9" was added as a theme that kept cropping up in students' use, for example of social media in the background as they worked on assignments.
The line between the use of social media for social and academic use is becoming blurred, as students report using social networking tools for both formal and informal academic work. This seems largely to be due to social media's affordances for ease of communication, efficient creation of academic groups and even saving money on MXit. This was reflected in student interviews and nodes for "Status update 2.24.10", "Messaging 2.24.11" and "Friending 2.24.12" were added, which could be applied to tracking affordances typical of social media.
Some first-year students also volunteered a fair amount of information on their preferences for response times ("Availability and feedback speed 2.25.11"), what they preferred to access services on ("Service preference 2.25.12"), how they felt about losing network access ("Mobile network access 2.25.13") and whether they experienced any limitations from their cellular provider ("Service limits 2.25.14").
Several students described having problems when using photocopying equipment for the first time ("Photocopies 2.31.7") and the importance of formal provision of either analogue and/or digital course material ("Textbooks and course reader 2.31.6").
Interviews revealed a wider range of actions with university software than initially identified, so the following nodes were added: "Group practicals 2.33.10", "Lecture notes 2.33.11", "Catch up missed classes 2.33.12", "Read announcements 2.33.13" and "Question and answer 2.33.14". And the following nodes were added under phases and types of academic use; "Frequency and duration of use 2.35.7", "Desired use 2.35.8" and "Self taught 2.35.9".
Future ICT Use coding index
 |
| Changes drawn on the coding index for Future ICT Use 3 (30 March, 2012) |
Due to having recently upgraded mobile, laptop or other ICT technology and/or experiencing financial constraints, some students indicated that they did not want an upgrade ("No new mobile phone upgrade desired 3.11.2", "No new laptop upgrade desired 3.12.2" and "No other ICT desired 3.13.2").
Some students spoke about their ambitions at university ("University ambitions 3.24"), as well as the services they wanted to be on ("Academic services 3.31.1" and "Personal services 3.31.2"). Another University of Cape Town student mentioned his community involvement and promotion of ICT, so the node "Community involvement 3.4" was added to reflect this.
Lastly, a node "Play at Conferences 4" has been added to track the most interesting segments of student interviews. These are intended to be exported and formatted for playing at conferences by the project's research lead, Laura Czerniewicz, or principal investigator, Cheryl Brown.
Labels:
academic
,
coding
,
nvivo
,
qualitative
,
research
,
software
,
students
,
university
Location: Cape Town, Western Cape Province, RSA
Cape Town, South Africa
Saturday, 17 March 2012
Four NVivo 9 tips to save you from trouble, and one from worry.
Written to save NVivo 9 users some trouble and worries.
I've been working with NVivo 9 for almost a year now and here are four important tips on what to do (and avoid). Plus a fifth on what not to worry about:
1. Work on your files locally, not via a network.
Although I was told this at an NVivo workshop last year, I proceeded to ignore it as working off a project file from the local area network folder seemed not to present any problems; it was responsive and saved me the time of backing up from my local drive. That was all good-and-well until I lost a whole day's work, because the file became corrupt! What caused this, I do not know: I suspect an automated Time Machine backup ran and NVivo subsequently froze. After restarting it, the file would not open and viewing the file's information showed it had shifted from being 180 MB big to 0 KB; not a good sign :(. I now only work locally and backup to the LAN at the end of each workday. Although this means adding an extra few minutes to my schedule, I can be confident of not losing nine hours!
2. If you work via a network, you can also expect big problems if you shut down your computer without closing NVivo properly.
Just in case the thought of losing your entire day's work won't persuade you, how about not being able to work on your file for the rest of the day?! When adding external speakers, I switched my Mac off by mistake. DOH! I was then unable to open the file off the network as I kept getting a message that it was "already in use". I then tried everything I could to circumvent this problem, to no avail (I was blocked from copying the file to another location as it's "in-use"; logging out of the LAN software; re-mapping the drive... even the old restart everything fail-safe failed.) So, the moral of the story is not to work off the network; if your computer's power shuts down unexpectedly, you may find it impossible to work on the same project file that day...
3. Set all automated tasks to run outside your NVivo sessions.
As an NVivo user on Mac, I must run NVivo 9 on Windows 7 above Parallels over MacOSX. And if the computer processing resources available to any one of these fails, NVivo sputters and does not work optimally. To limit this danger, I take these preventative measures:
4. Save a new version of your file each day.
It's a good practice to change your filename for each day. In my case, I simply change the daily date I type in the filename; i.e. "17 Mar 2012 ICT Access and Use UCT". I then backup the file to the relevant project month folder on the network. This ensures that I have the a backup record and can easily show the progress on the work I'm paid by the hour to do. It is also useful when working with other people on the same project file; for example, being a fallback just in case certain attributes are not imported.
5. Don't be afraid to import many, large video files as internal source.
If you want full coding functionality, you should always import files as internal sources, not as externals. Originally, I thought that importing a file as internal source automatically meant that the video was saved into the NVivo file itself. So, I thought I must limit myself to only importing the most interesting videos as internal source. However, through experimentation, I soon learnt that one could use the 62-bit version to import files much larger than NVivo 9's guidelines stated AND many of them (see the screengrab below), without the project file's size growing substantially.
The NVivo file above is just 170 MB in size; you don't have to take my word for it, see below.
As long as the location of the source video remains the same, there are no issues. Now, since the maximum file size of an NVivo project is reportedly 2 GB, I can add many, many more video interviews as internal source. So, with a nod to QSR International's Australian pedigree, it's a happy case of "No worries, mate!"
So, those are the most important tips I have learnt and if you have other ones to share, feel free to submit them via the comments box below, thanks.
As an NVivo user on Mac, I must run NVivo 9 on Windows 7 above Parallels over MacOSX. And if the computer processing resources available to any one of these fails, NVivo sputters and does not work optimally. To limit this danger, I take these preventative measures:
- I ensure that all the computers' backups and software updates (PC and Mac) either run outside my work hours or must be manually activated.
- I do not run more than three software packages simultaneously.
- I run NVivo in full screen (not Coherence) mode in Parallels almost all the time, so there's no temptation to run several Mac and PC applications simultaneously.
4. Save a new version of your file each day.
It's a good practice to change your filename for each day. In my case, I simply change the daily date I type in the filename; i.e. "17 Mar 2012 ICT Access and Use UCT". I then backup the file to the relevant project month folder on the network. This ensures that I have the a backup record and can easily show the progress on the work I'm paid by the hour to do. It is also useful when working with other people on the same project file; for example, being a fallback just in case certain attributes are not imported.
5. Don't be afraid to import many, large video files as internal source.
If you want full coding functionality, you should always import files as internal sources, not as externals. Originally, I thought that importing a file as internal source automatically meant that the video was saved into the NVivo file itself. So, I thought I must limit myself to only importing the most interesting videos as internal source. However, through experimentation, I soon learnt that one could use the 62-bit version to import files much larger than NVivo 9's guidelines stated AND many of them (see the screengrab below), without the project file's size growing substantially.
 |
| Screengrab of ICT Access and Use video interview imports (17 March 2012) |
As long as the location of the source video remains the same, there are no issues. Now, since the maximum file size of an NVivo project is reportedly 2 GB, I can add many, many more video interviews as internal source. So, with a nod to QSR International's Australian pedigree, it's a happy case of "No worries, mate!"
So, those are the most important tips I have learnt and if you have other ones to share, feel free to submit them via the comments box below, thanks.
Labels:
nvivo
,
qualitative
,
research
,
software
Location: Cape Town, Western Cape Province, RSA
Cape Town, South Africa
Subscribe to:
Comments
(
Atom
)

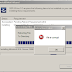






 orcid.org/0000-0001-9566-8983
orcid.org/0000-0001-9566-8983