Saturday, 29 March 2025
Techniques for suppressing health experts' social media accounts, part 1 - The Science™ versus key opinion leaders challenging the COVID-19 narrative
There has been extensive censorship of legitimate, expert criticism during the COVID-19 event (Kheriaty, 2022. Shir-Raz et al, 2023. Hughes, 2024). Such scientific suppression makes the narrow frame visible for what the sponsors of global health authoritarianism permit for questioning of The Science™. In contrast to genuine science which innovates through critique, incorporated science does not welcome questioning. Like fascism, corporatist science views critiques of its interventions to be heresy. In the COVID-19 event, key opinion leaders who criticised the lack of scientific rigour behind public health measures (such as genetic vaccine mandates) were treated as heretics by a contemporary version of the Inquisition (Malone et al., 2024). Dissidents were accused of sharing "MDM" (Misinformation, Disinformation and Malinformation) assumed to place the public's lives at risk. Particularly in prestigious medical universities, questioning the dictates of health authorities and their powerful sponsors was viewed as being unacceptable, completely outside an Overton Window that had become far more restrictive due to fear- mongering around a "pandemic" (see Figure 1).
Higher Education is particularly susceptible to this groupthink, as it lends itself to a purity spiral, which in turn contributes to the growing spiral of silence for "unacceptable views". A purity spiral is a form of groupthink in which it is more beneficial to hold some views than to not hold them. In a process of moral outbidding, individual academics with more extreme views are rewarded. This was evidenced at universities where genetic vaccine proponents loudly supported the mandatory vaccination of students, despite them having minimal, if any, risk. In contrast, scholars expressing moderation, doubt or nuance faced ostracism as "anti-vaxxers". In universities, there are strong social conformity factors within its tight-knit community. Grants, career-support and other forms of institutional support depend on collegiality and alignment with prevailing norms. Being labeled a contrarian for questioning a ‘sacred cow’, such as "safe and effective" genetic vaccines, is likely to jeopardise one’s reputation, and academic future. Academic disciplines coalesce around shared paradigms and axiomatic truths, routinely amplifying groupthink. Challenging reified understandings as shibboleths can lead to exclusion from conferences, journals and cost scholars departmental, faculty, and even university support. Particularly where powerful funders object to such dissent!
Here, administrative orthodoxy can signal an “official” position for the university that chills debate. Dissenters fears of isolation and reprisal (such as poor evaluations and formal complaints for not following the official line) may convince them to self-censor. Particularly where the nonconformist assesses that the strength of opinion against his or her opinion is virulent, alongside high costs to expressing a disagreeable viewpoint- such as negotiating cancelation culture. Individuals who calculate that they have a low chance of success to convince others, and are likely to pay a steep price, self censor and contribute to the growing spiral of silence. The COVID-19 event serves as an excellent example for this growing spiral’s chilling effect versus free speech and independent enquiry.
COVID-19 is highly pertinent for critiquing censorship in the Medical and Health Sciences. Particularly as it featured conflicts of interest that contributed to global health "authorities" policy guidance. Notably, the World Health Organisation promoted poorly substantiated and even unscientific guidelines (Noakes et al., 2021), that merit being considered MDM. In following such dictates from the top policy makers of the Global Public-Private Partnership (GPPP or G3P), most governments' health authorities seemed to ignore key facts. Notably: i. COVID-19 risk was steeply age-stratified (Verity et al, 2019. Ho et al, 2020. Bergman et al, 2021); ii. Prior COVID-19 infection can provide substantial immunity (Nattrass et al., 2021); iii. COVID-19 genetic vaccines did not stop disease transmission (Eyre et al. 2022, Wilder-Smith, 2022); iv. mass-masking was ineffective (Jefferson et al., 2023. Halperin, 2024); v. school closures were unwarranted (Wu et al., 2021); and, vi. there were better alternatives to lengthy, whole-society lockdowns (Coccia, 2021, Gandhi and Venkatesh, 2021. Herby et al., 2024). Both international policy makers' and local health authorities' flawed guidance must be open debate and rigorous critique. If public health interventions had been adapted to such key facts during the COVID-19 event, the resultant revised guidance could well have contributed to better social-, health-, and economic outcomes for billions of people!
This post focuses on six types of suppression techniques that were used against dissenting accounts whose voices are deemed illegitimate "disinformation" spreaders by the Global public-Private Partnerships (G3P)-sponsored industrial censorship complex. This an important concern, since claims that the suppression of free speech's digital reach can "protect public safety" were proved false during COVID-19. A case in point is the censorship of criticism against employee's vaccine mandates. North American employers' mandates are directly linked to excess disabilities and deaths for hundreds and thousands of working-age employees (Dowd, 2024). Deceptive censorship of individuals' reports of vaccine injuries as "malinformation", or automatically-labelling criticism of Operation Warp Speed as "disinformation", would hamper US employee's abilities to make fully-informed decisions on the safety of genetic vaccines. Such deleterious censorship must be critically examined by academics. In contrast, 'Disinformation-for-hire' scholars (Harsin, 2024) will no doubt remain safely ensconced behind their profitable MDM blinkers.
This post is the first in a series that spotlights the myriad of account suppression techniques that exist. For each, examples of censorship against health experts' opinions are provided. Hopefully, readers can then better appreciate the asymmetric struggle that dissidents face when their accounts are targeted by the censorship industrial complex with a myriad of these strategies spanning multiple social media platforms:
Practices for @Account suppression
#1 Deception - users are not alerted to unconstitutional limitations on their free speech
#2 Cyberstalking - facilitating the virtual and physical targeting of dissidents
#3 Othering - enabling public character assassination via cyber smears
#4 Not blocking impersonators or preventing brandjacked accounts
Instead of blanket censorship, I am having YouTube bury all my actual interviews/content with videos that use short, out of context clips from interviews to promote things I would never and have never said. Below is what happens when you search my name on YouTube, every single… pic.twitter.com/xNGrfMMq52
— Whitney Webb (@_whitneywebb) August 12, 2024
Instead of blanket censorship, I am having YouTube bury all my actual interviews/content with videos that use short, out of context clips from interviews to promote things I would never and have never said. Below is what happens when you search my name on YouTube, every single… pic.twitter.com/xNGrfMMq52
— Whitney Webb (@_whitneywebb) August 12, 2024Whether such activities are from intelligence services or cybercriminals, they are very hard for dissidents and/or their representatives to respond effectively against. Popular social media companies (notably META, X and TikTok) seldom respond quickly to scams, or to the digital "repersoning" discussed in a Corbett Report discussion between James Corbett and Whitney Webb.
In Corbett's case, after his account was scrubbed from YouTube, many accounts featuring his identity started cropping up there. In Webb's case, she does not have a public profile outside of X, but these were created featuring her identity on Facebook and YouTube. "Her" channels clipped old interviews she did and edited them into documentaries on material Whitney has never publicly spoken about, such as Bitcoin and CERN. They also misrepresented her views on the transnational power structure behind the COVID-19 event, suggesting she held just Emmanuel Macron and Klaus Schwab responsible for driving it. They used AI thumbnails of her, and superimposed her own words in the interviews. Such content proved popular and became widely reshared via legitimate accounts, pointing to the difficulty of dissidents countering it. She could not get Facebook to take down the accounts, without supplying a government-issued ID to verify her own identity.
Digital platforms may be disinterested in offering genuine support- they may not take any corrective action when following proxy orders from the US Department of State (aka 'jawboning') or members of the Five Eyes (FVEY) intelligence agency. In stark contrast to marginalised dissenters, VIPS in multinationals enjoy access to online threat protection services (such as ZeroFox) for executives that cover brandjacking and over 100 other cybercriminal use-cases.
#5 Filtering an account's visibility through ghostbanning
As the Google Leaks (2019) and Facebook- (2021) and Twitter Files (2022) revelations have spotlighted, social media platforms have numerous algorithmic censorship options, such as the filtering the visibility of users' accounts. Targeted users may be isolated and throttled for breaking "community standards" or government censorship rules. During the COVID-19 event, dissenters' accounts were placed in silos, de-boosted, and also subject to reply de-boosting. Contrarians' accounts were subject to ghostbanning (AKA shadow-banning)- this practice will reduce an account’s visibility or reach secretly, without explicitly notifying its owner. Ghostbanning limits who can see the posts, comments, or interactions. This includes muting replies and excluding targeted accounts' results under trends, hashtags, searches and in followers’ feeds (except where users seek a filtered account's profile directly). Such suppression effectively silences a user's digital voice, whilst he or she continues to post under the illusion of normal activity. Ghostbanning is thus a "stealth censorship" tactic linked to content moderation agendas.
This term gained prominence with the example of the Great Barrington Declaration's authors, Professors Jay Bhattacharya, Martin Kulldorff, and Sunetra Gupta. Published on October 4, 2020, this public statement and proposal flagged grave concerns about the damaging physical and mental health impacts of the dominant COVID-19 policies. It argued that an approach for focused protection should rather be followed than blanket lockdowns, and that allowing controlled spread among low-risk groups would eventually result in herd immunity. Ten days later, a counter- John Snow Memorandum was published in defence of the official COVID-19 narrative's policies. Mainstream media and health authorities amplified it, as did social media given the memorandum's alignment with prevailing platform policies against "misinformation" circa-2020. In contrast, the Great Barrington Declaration was targeted indirectly through platform actions against its proponents and related content:
Stanford Professor of Medicine, Dr Jay Bhattacharya’s Twitter account was revealed (via the 2022 Twitter Files) to have been blacklisted, reducing its visibility. His tweets questioning lockdown efficacy and vaccine mandates were subject to algorithmic suppression. Algorithms could flag his offending content with terms like “Visibility Filtering” (VF) or “Do Not Amplify”, reducing its visibility. For instance, Bhattacharya reported that his tweets about the Declaration and seroprevalence studies (showing wider COVID-19 spread than official numbers suggested) were throttled. Journalist Matt Taibbi's reporting on the "Twitter Files" leaks confirmed that Twitter had blacklisted Prof Bhattacharya's account, limiting its reach due to his contrarian stance. YouTube also removed videos in which he featured, such as interviews in which he criticised lockdown policies.
The epidemiologist and biostatistician, Prof Kulldorff observed that social media censorship stifled opportunities for scientific debate. He experienced direct censorship on multiple platforms, which included shadowbans. Twitter temporarily suspended his account in 2021 for tweeting that not everyone needed the COVID-19 vaccine ('Those with prior natural infection do not need it. Nor children'). Posts on X and web reports indicate Kulldorff was shadowbanned beyond this month-long suspension. The Twitter Files, released in 2022, revealed he was blacklisted, meaning his tweets’ visibility was algorithmically reduced. Twitter suppressed Kulldorff's accurate genetic vaccine critique, preventing comments and likes. Internal Twitter flags like “Trends Blacklisted” or “Search Blacklisted” (leaked during the 2020 Twitter hack) suggest Kulldorff's account was throttled in searches and trends, a hallmark of shadowbanning where reach is curtailed without notification. Algorithmic deamplification excluded Prof Kulldorff's tweets from being seen under trends, search results, or followers’ feeds- except where users sought his profile directly. This reflects how social media companies may apply visibility filters (such as a Not Safe For Work (NSFW) view). Kulldorff also flagged that LinkedIn’s censorship pushed him to platforms like Gab, implying a chilling effect on his professional network presence.
An Oxford University epidemiologist, Professor Gupta faced less overt account-level censorship, but still had to negotiate content suppression. Her interviews and posts on Twitter advocating for herd immunity via natural infection amongst the young and healthy were often flagged, or down-ranked.
#6 Penalising accounts that share COVID-19 "misinformation"
Do share your views by commenting below, or reply to this tweet thread at https://x.com/travisnoakes/status/1906250555564900710.
Saturday, 15 April 2023
Use the Shushmoji app to learn anti chat harassment tactics and end anti-social conversations with WhatsApp chat stickers
| Stop silly troll! chat sticker example | Stop sinner! chat sticker example | |
|---|---|---|
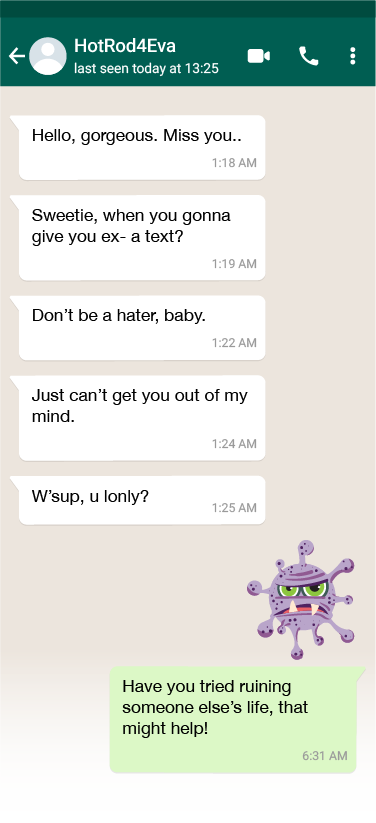 |  |
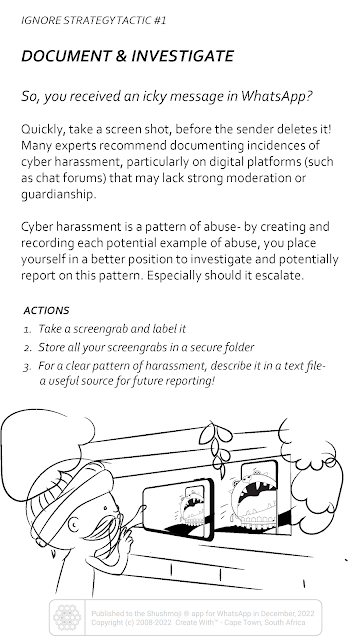
The Shushmoji app also offers twenty anti-chat harassment tactics cards. These fall under four strategies for stopping trolls: ignore, report, respond and prevent. Install the app to scroll through all twenty cards on your phone or tablet.
| Ignore strategy index card | Ignore tactic card |
|---|---|
Why develop a Shushmoji app?
Being silent echoes the conventional advice, Do Not Feed the Trolls (DNFTT). It reflects how there are many downsides to communicating with harassers, since they are likely to be mentally unstable (Barnes, 2018). Online trolls score low in the Big Five Personality scores of agreeability and conscientiousness, but score high in Dark Tetrad traits of- narcissism, Machiavellianism, sub-clinical psychopathy and/or everyday sadism. Attempting rational engagement with perpetrators of cyber harassment is likely to provoke retaliatory attacks in excess of the original abuse. This may be further escalated via circling cyber vultures and mobs. Such amplification is common to unmoderated platforms where destructive, hostile and bigoted behaviour is rewarded with likes and re-shares.
Create With Cape Town's end-of-conversation stickers were designed to support targets' ability to disengage from cyberbullies. Unlike the DNFTT tactic, it does not mute their voice and right-of-reply.
These chat stickers can help end chats-gone-bad, whilst showing trolls and their audiences what one thinks of their behaviour.
Support using the Shushmoji app
Shushmoji app credits
Shushmoji feedback
Alternately, hashtag #Shushmoji and #CreateWithCapeTown and give a shout-out to our Facebook, Instagram, LinkedIn or Twitter accounts. Cheers!
Friday, 26 August 2022
Want emoji stickers to end #WhatsApp chats with #cyberbullies? The #Shushmoji app on #Android is here!
Saturday, 23 April 2022
Eight conceptual challenges in developing the 'online academic bullying' framework
1 NEW FORMS OF POWER IMBALANCE
 |
| Figure 1. Faculties and departments in which employees persistently criticised the Emeritus Professor on social media (Travis Noakes, 2020) |
Attacking a scientific dissident as a pre-defined target seemed to provide attackers with an instant form of credibility- they did not have to prove their symbolic credentials to gain visibility. Few of the professor's blogging critics were Health Science scholars. Despite making no scholarly contribution to the debate, some academic cyberbullies seemed to achieve visibility as opinion "leaders" online. This shows how micro-celebrity hijacking can apply for Higher Education (HE) employees. Academic bloggers criticise public intellectuals for "wrongthink" thereby gaining attentional capital- blogged critiques by "independent" critical thinkers can convert into appearances on broadcast media.
Another dimension of power imbalance may lie in technical cultural capital- an OAB recipient who has less knowledge of the digital platform(s) on which she is being attacked may be at a serious disadvantage. For example, cyberbullies can use advantages in their ‘digital dimensions’ (Paino & Renzulli, 2013) of cultural capital for gaining greater visibility. They can leverage a myriad of online presences for amplifying their attacks, whilst leveraging multiple chains of digital publication that are difficult for a victim to reply to.
This suggests another imbalance whereby OAB recipients will struggle to defend themselves against asymmetrical cyber-critiques. It may be exhausting to respond to frequent criticisms, across a myriad of digital platforms and conflicting timezones.
2 BEYOND TROLLS: ACADEMIC CYBERBULLIES AS DECEIVERS, FLAMERS, ETC.
3 SCIENTIFIC SUPPRESSION VERSUS BIO-MEDICAL HERESY "JUSTIFIES" HARASSMENT
4 FOREGROUNDING THE VICTIM’S PERSPECTIVE
In university workplaces, bullies can use a justification of “academic freedom” to condone actions that would be unacceptable in other workplaces (Driver, 2018). For example, an academic lecturer (who is neither a scholar nor a scientist) published thirty blog posts that criticised the Emeritus Professor's popularisation of LCHF science. Although by no means an academic peer, this junior lecturer might justify such fervent criticism of a fellow employee at the same university as a necessary part of academic freedom in an institute of higher learning. Nevertheless, such obsessive behaviour from a low-ranking, under-qualified employee seems unlikely to be acceptable at any other place of employment.
6 GUARDIANS AGAINST VICTIMS OF ACADEMIC BULLYING
8 A COMPLEX FORM FOR AN EXTREME CASE
GRAPHIC CREDITS
Stop, academic bully! shushmoji™ graphics courtesy of Create With Cape Town.
Wednesday, 24 November 2021
Shushmoji app briefing presentation to Younglings' interns and mobile dev leadership
Written for interns at Younglings who expressed an interest in working on the Shushmoji app for Android and Apple
I recently presented on the background to Create With's Shushmoji app to Younglings. Its interns will be working to complete an Android version this year and an Apple version for launch in 2022.
The hyperlinks from the presentation are shared below for ease-of-access:
SLIDE 3
Travis Noakes' research at www.travisnoakes.co.za/p/researcher.html
Create With at createwith.net/
SLIDE 4
Anti-trolling graphics to end abusive conversations at samultimodality.wordpress.com/2018/11/26/anti-trolling-graphics-to-end-abusive-conversations-how-to-whack-a-troll/
Strategies against cyber harassment at http://bit.ly/2D8qv0k


















 orcid.org/0000-0001-9566-8983
orcid.org/0000-0001-9566-8983